At the beginning of May, about 230,000 computers in more than 150 countries were infected with a ransomware virus. Before the victims had time to eliminate the consequences of this attack, a new one, called Petya, followed. The largest Ukrainian and Russian companies, as well as government agencies.
The Ukrainian cyber police established that the virus attack began through an accounting update mechanism. software M.E.Doc, which is used to prepare and send tax reports. Thus, it became known that the networks of Bashneft, Rosneft, Zaporozhyeoblenergo, Dneproenergo and the Dnieper Electric Power System did not escape infection. In Ukraine, the virus penetrated government computers, PCs of the Kyiv metro, telecom operators and even the Chernobyl nuclear power plant. In Russia, Mondelez International, Mars and Nivea were affected.
The Petya virus exploits the EternalBlue vulnerability in the Windows operating system. Symantec and F-Secure experts say that although Petya encrypts data like WannaCry, it is still somewhat different from other types of encryption viruses. "The Petya virus is new look extortion with malicious intent: it does not just encrypt files on the disk, but locks the entire disk, making it practically unusable, F-Secure explains. “Specifically, it encrypts the MFT master file table.”
How does this happen and can this process be prevented?
Virus "Petya" - how does it work?
The Petya virus is also known by other names: Petya.A, PetrWrap, NotPetya, ExPetr. Once it gets into the computer, it downloads ransomware from the Internet and tries to attack part of the hard drive with the data necessary to boot the computer. If he succeeds, then the system issues Blue Screen of Death(" blue screen death"). After reboot, a message appears about checking hard disk with a request not to turn off the power. Thus, the ransomware pretends to be system program to check the disk, encrypting files with certain extensions at this time. At the end of the process, a message appears indicating that the computer is blocked and information on how to obtain a digital key to decrypt the data. The Petya virus demands a ransom, usually in Bitcoin. If the victim does not have a backup copy of his files, he is faced with the choice of paying $300 or losing all information. According to some analysts, the virus is only masquerading as ransomware, while its true goal is to cause massive damage.
How to get rid of Petya?
Experts have discovered that Petya virus looking for local file and, if the file already exists on disk, exits the encryption process. This means that users can protect their computer from ransomware by creating this file and setting it as read-only.
Although this clever scheme prevents the ransomware process from starting, this method can be considered more like a “computer vaccination”. Thus, the user will have to create the file themselves. You can do this as follows:
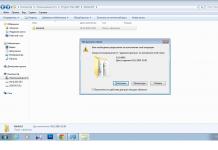
- First you need to understand the file extension. In the Folder Options window, make sure that the Hide extensions for known file types checkbox is unchecked.
- Open the C:\Windows folder, scroll down until you see the notepad.exe program.
- Left click on notepad.exe, then press Ctrl + C to copy and then Ctrl + V to paste the file. You will receive a request asking for permission to copy the file.
- Click the Continue button and the file will be created as a notepad - Copy.exe. Left-click on this file and press F2, then erase the file name Copy.exe and enter perfc.
- After changing the file name to perfc, press Enter. Confirm the rename.
- Now that the perfc file has been created, we need to make it read-only. To do this, right-click on the file and select “Properties”.
- The properties menu for this file will open. At the bottom you will see "Read Only". Check the box.
- Now click the Apply button and then the OK button.
Some security experts suggest creating C:\Windows\perfc.dat and C:\Windows\perfc.dll files in addition to the C:\windows\perfc file in order to more thoroughly protect against the Petya virus. You can repeat the above steps for these files.
Congratulations, your computer is protected from NotPetya/Petya!
Symantec experts offer some advice to PC users to prevent them from doing things that could lead to locked files or loss of money.
- Don't pay money to criminals. Even if you transfer money to the ransomware, there is no guarantee that you will be able to regain access to your files. And in the case of NotPetya / Petya, this is basically meaningless, because the goal of the ransomware is to destroy data, and not to get money.
- Make sure you create regularly backups data. In this case, even if your PC becomes the target of a ransomware virus attack, you will be able to recover any deleted files.
- Don't open emails with dubious addresses. Attackers will try to trick you into installing malware or try to obtain important data for attacks. Be sure to inform IT specialists if you or your employees receive suspicious emails or links.
- Use reliable software. Timely updating of antivirus software plays an important role in protecting computers from infections. And, of course, you need to use products from reputable companies in this field.
- Use mechanisms to scan and block spam messages. Incoming emails should be scanned for threats. It is important that any types of messages that contain links or typical keywords phishing.
- Make sure all programs are up to date. Regular remediation of software vulnerabilities is necessary to prevent infections.
Should we expect new attacks?
The Petya virus first appeared in March 2016, and security specialists immediately noticed its behavior. The new Petya virus infected computers in Ukraine and Russia at the end of June 2017. But this is unlikely to be the end. Hacker attacks using ransomware viruses similar to Petya and WannaCry will be repeated, said Stanislav Kuznetsov, deputy chairman of the board of Sberbank. In an interview with TASS, he warned that such attacks will definitely happen, but it is difficult to predict in advance in what form and format they may appear.
If, after all the cyber-attacks that have passed, you have not yet taken at least the minimum steps to protect your computer from a ransomware virus, then it is time to get serious about it.
Scary computer virus turned out to be even worse - what’s wrong with the new ransomware Trojan, why it was called Petya and how it infected entire networks so quickly reputable companies? About this right now in the Vesti.net program.
The epidemic outbreak of infections with the Petya ransomware virus turned out to be a much more serious blow than previously thought. There is a high probability that the functionality of the affected systems will not be restored. Neither paying the ransom nor waiting for a decision from specialists.
"The Trojan encrypts files; if it has enough rights, it can encrypt the main boot area of the disk. And upon detailed analysis, it turned out that it is impossible to decrypt the main boot area of the disk. Because there is simply no such functionality. The key that can be used to decrypt is unknown. Why is this what was done is not known for certain.
It could be like simple mistake because for some reason they were in a hurry to carry out the attack and did not test it, or perhaps it was the second option - a distracting maneuver, to show everyone that this is an encryptor, a second WannaCry, so that everyone would puzzle over decryption, pay/not pay. But there was a true goal. Perhaps out of many victims, only one organization was targeted. All the rest were just a diversion.
And the Petya virus itself turned out to be not Petya. And not a modification of the WannaCry malware that caused a lot of noise a month ago, as was initially assumed. As it turned out after a detailed study of the code of the malicious program, under the Petya Trojan known to specialists, new virus only disguised itself, so it was called ExPetya. And what it has in common with the already famous WannaCry is the use of a vulnerability from the stolen and declassified arsenal of the NSA.
Vyacheslav Zakorzhevsky, head of the anti-virus research department at Kaspersky Lab:
"ExPetya uses EternalBlue. Slightly modified. But also another vulnerability from the same set published by The Shadow Brokers. That is, they used not only the same as WannaCry, but also brought to mind the second vulnerability, which we have not seen from anyone cryptographerWe see that a number of advanced writing techniques were used, including the attackers were able to modify Eternalromance, EternalBlue, add a number of tools for stealing login passwords and remotely launching corporate network. These are clearly not schoolchildren, not students. These should be professional programmers who know what they are doing. And rather, it was not one person, but several, each with their own specialization."
Just like Eternal, ExPetya also caused the most problems for large companies. A month ago, only in Russia, for example, law enforcement systems, as well as the Megafon operator, became victims of ransomware. This time, the scale of infection and the status of the victims were similar: Rosneft and Bashneft in Russia, in Ukraine - local energy networks, Boryspil airport, post office, network of the Cabinet of Ministers. then Europe got it too.
But the way the virus spread turned out to be different. For example, attackers managed to infect a Ukrainian program for accounting M.E.Doc. That is, the corporate networks of everyone who installed official update M.E.Doc were immediately infected and blocked.
Vyacheslav Zakorzhevsky, head of the anti-virus research department at Kaspersky Lab:
"The fact is that this Trojan has the ability to spread across a corporate network, and at home, without using vulnerabilities. Let me explain: one vulnerable computer on the network is enough. If the encryptor gets there, it can steal a login and password and spread further across the network without vulnerabilities. That is, if a large fleet of machines is combined into one network and at least one computer is not protected and updated, then this will open the way for the Trojan. This is different from WannaCry, which used only one EternalBlue vulnerability.
ExPetya (by the way, Petya is not a hint of Russian origin, but a reference to the name of the military satellite from Bond) is already the second large-scale attack using the NSA’s cyber arsenal. This means that these tools, which target older versions of Windows, are not outdated as many have claimed. That is, Windows 7, Vista and XP are still quite relevant for many corporations, and for some reason they don’t even update them.
According to Positive Technologies, over 80 organizations in Russia and Ukraine were affected by Petya’s actions. Compared to WannaCry, this virus is considered more destructive, as it spreads using several methods: using Windows Management Instrumentation, PsExec and EternalBlue exploit. In addition, the ransomware is embedded free utility Mimikatz.
“This set of tools allows Petya to remain operational even in those infrastructures where the lesson of WannaCry was taken into account and the appropriate security updates were installed, which is why the encryptor is so effective,” Positive Technologies said.
As the head of the threat response department told Gazeta.Ru information security Elmar Nabigaev company,
If we talk about the reasons for the current situation, then the problem is again a careless attitude towards information security problems.
The head of the Avast virus laboratory, Jakub Kroustek, in an interview with Gazeta.Ru, said that it is impossible to establish for certain who exactly is behind this cyber-attack, but it is already known that the Petya virus is distributed on the darknet using the RaaS (malware as a service) business model.
“So, the share of program distributors reaches 85% of the ransom, 15% goes to the authors of the ransomware virus,” Kroustek said. He noted that the Petya authors provide all the infrastructure, C&C servers and money transfer systems, which helps attract people to spread the virus, even if they have no programming experience.
In addition, Avast told which operating systems were most affected by the virus.
Windows 7 was in first place - 78% of all infected computers. Next comes Windows XP (18%), Windows 10 (6%) and Windows 8.1 (2%).
Kaspersky Lab considered that although the virus is similar to the Petya family, it still belongs to a different category, and gave it a different name - ExPetr, that is, “former Peter.”
Deputy Director for Development of the Aideko company Dmitry Khomutov explained to the Gazeta.Ru correspondent that cyber attacks WannaCry viruses and Petya led to what “I had been warning about for a long time,” that is, to the global vulnerability of information systems used everywhere.
“Loopholes left by American corporations for intelligence agencies became available to hackers and were quickly combined with the traditional arsenal of cybercriminals - ransomware, botnet clients and network worms,” said Khomutov.
Thus, WannaCry taught the global community virtually nothing - computers remained unprotected, systems were not updated, and efforts to release patches even for outdated systems simply went to waste.
Experts urge not to pay the required ransom in bitcoins, since the email address that the hackers left for communication was blocked by the local provider. Thus, even in the case of “honest and good intentions” of cybercriminals, the user will not only lose money, but will also not receive instructions to unlock his data.
Petya harmed Ukraine the most. Among the victims were Zaporozhyeoblenergo, Dneproenergo, Kiev Metro, Ukrainian mobile operators Kyivstar, LifeCell and Ukrtelecom, Auchan store, Privatbank, Boryspil airport and others.
Ukrainian authorities immediately blamed Russia for the cyberattack.
“War in cyberspace, spreading fear and terror among millions of users personal computers and applying straight material damage due to the destabilization of the work of business and government agencies, this is part of the overall strategy of the hybrid war of the Russian empire against Ukraine,” said the Rada deputy from the Popular Front.
Ukraine may have been hit harder than others due to the initial spread of Petya through automatic update M.E.doc - programs for financial reporting. This is how Ukrainian departments, infrastructure facilities and commercial companies were infected - they all use this service.
The ESET Russia press service explained to Gazeta.Ru that in order to infect a corporate network with the Petya virus, one vulnerable computer that does not have security updates installed is sufficient. With his help malware will enter the network, receive administrator rights and spread to other devices.
However, M.E.doc issued an official refutation of this version.
“Discussion of the sources of occurrence and spread of cyber attacks is actively carried out by users on social networks, forums and other information resources, in the wording of which one of the reasons is the installation of updates to the M.E.Doc program. M.E.Doc development team refutes this information and states that such conclusions are clearly erroneous, because the developer M.E.Doc, as a responsible supplier software product, monitors safety and cleanliness own code", says the
Companies around the world on Tuesday, June 27, suffered from a large-scale cyberattack of malware spreading through email. The virus encrypts user data on hard drives and extorts money in bitcoins. Many immediately decided that this was the Petya virus, described back in the spring of 2016, but antivirus manufacturers believe that the attack occurred due to some other, new malware.
A powerful hacker attack on the afternoon of June 27 hit first Ukraine, and then several large Russian and foreign companies. The virus, which many mistook for last year's Petya, is spreading on computers with operating system Windows via a spam email with a link that, when clicked, opens a window requesting administrator rights. If the user allows the program access to his computer, the virus begins to demand money from the user - $300 in bitcoins, and the amount doubles after some time.
The Petya virus, discovered in early 2016, spread according to exactly the same pattern, so many users decided that this was it. But specialists from antivirus software development companies have already stated that some other, completely new virus, which they will still study, is to blame for the attack. Experts from Kaspersky Lab have already given unknown virus name - NotPetya.
According to our preliminary data, this is not the Petya virus, as mentioned earlier, but a new malware unknown to us. That's why we called it NotPetya.
The Dr.Web company also writes that although the virus is similar to Petya in appearance, in fact this malware has never been encountered by specialists and is fundamentally different from Petya, but what exactly remains to be determined.
Analysts are currently investigating the new Trojan; we will provide details later. Some media sources draw parallels with the Petya ransomware (detected by Dr.Web in particular as Trojan.Ransom.369) in connection with the external manifestations of the ransomware, however, the method of spreading the new threat differs from the standard scheme used by Petya.
Dr.Web and Kaspersky Lab also reminded users about simple rules, which would help avoid virus infection of many computers. Antivirus software companies have talked about them, but not all people still follow them.
Dr.Web urges all users to be careful and not open suspicious emails (this measure is necessary, but not sufficient). You should also back up your critical data and install any security updates for your software. The presence of an antivirus in the system is also required.
If your computer is already infected, then a solution has also been found. Back in April, the Geektimes portal published instructions on how to get rid of the virus. The first (complicated) method is to insert the infected media into another PC and “extract certain data from certain sectors of the infected hard drive”, and then pass “through a Base64 decoder and send to the site for processing.”
Virus "Petya": how not to catch it, how to decipher where it came from - the latest news about the Petya ransomware virus, which by the third day of its “activity” infected about 300 thousand computers in different countries world, and so far no one has stopped him.
Petya virus - how to decrypt, latest news. After an attack on a computer, the creators of the Petya ransomware demand a ransom of $300 (in bitcoins), but there is no way to decrypt the Petya virus, even if the user pays money. Kaspersky Lab specialists, who saw differences in the new virus from Petit and named it ExPetr, claim that decryption requires a unique identifier for a specific Trojan installation.
In previously known versions of similar encryptors Petya/Mischa/GoldenEye, the installation identifier contained the information necessary for this. In the case of ExPetr, this identifier does not exist, writes RIA Novosti.
The “Petya” virus – where it came from, the latest news. German security experts have put forward the first version of where this ransomware came from. In their opinion, the Petya virus began to spread through computers when M.E.Doc files were opened. This is an accounting program used in Ukraine after the ban on 1C.
Meanwhile, Kaspersky Lab says that it is too early to draw conclusions about the origin and source of spread of the ExPetr virus. It is possible that the attackers had extensive data. For example, email addresses from the previous newsletter or some others effective ways penetration into computers.
With their help, the “Petya” virus hit Ukraine and Russia, as well as other countries, with its full force. But the real scale of this hacker attack will be clear in a few days - reports.
“Petya” virus: how not to catch it, how to decipher it, where it came from - latest news about the Petya ransomware virus, which has already received a new name from Kaspersky Lab – ExPetr.