A sniffer is not always malicious. In reality, given type The software is often used to analyze network traffic in order to detect and correct anomalies and ensure uninterrupted operation. However, the sniffer can be used with malicious intent. Sniffers analyze everything that passes through them, including unencrypted passwords and credentials, so hackers who have access to the sniffer can get hold of users' personal information. In addition, the sniffer can be installed on any computer connected to the local network without the need to install it on the device itself - in other words, it cannot be detected during the entire connection time.
Where do sniffers come from?
Hackers use sniffers to steal valuable data by monitoring network activity and collecting personal information about users. Typically, attackers are most interested in user passwords and credentials in order to use them to gain access to online banking and online shopping accounts. Most often, hackers install sniffers in places where unprotected Wi-Fi connections for example in cafes, hotels and airports. Sniffers can disguise themselves as a connected device in a so-called spoofing attack in order to steal valuable data.
How to recognize a sniffer?
Unauthorized sniffers are extremely difficult to recognize virtually, as they can be installed almost anywhere, posing a very serious threat network security... Ordinary users often do not have the slightest chance of recognizing a sniffer tracking their network traffic. It is theoretically possible to install your own sniffer that would monitor all DNS traffic for the presence of other sniffers, but for an ordinary user it is much easier to install anti-sniffing software or an antivirus solution that includes network activity protection in order to stop any unauthorized intrusion or hide your network activities.
How to remove a sniffer
You can use a highly effective antivirus to detect and remove all types of sniffing malware installed on your computer. However, for complete removal sniffer from the computer, you must delete absolutely all folders and files related to it. It is also highly recommended to use an antivirus with a network scanner that will thoroughly check local area network for vulnerabilities and will instruct you on further actions if they are found.
How to avoid becoming a victim of a sniffer
- Encrypt all information you send and receive
- Scan your local network for vulnerabilities
- Use only verified and secured Wi-Fi networks
Protect yourself from sniffers
The first thing a user can do to protect himself from sniffers is to use a high-quality antivirus, like free antivirus Avast, which is able to thoroughly scan the entire network for security problems. An additional and highly effective way to protect information from sniffing is to encrypt all sent and received data online, including emails. mail. Avast SecureLine allows you to securely encrypt all data exchange and perform actions online with 100% anonymity.
Before you is a good sniffer (network traffic analyzer, with its help you can intercept information), which will allow you to receive quite complete information about all packets passing through the protocol of your choice in a visual video, in full news you can easily download IP Sniffer... The developers have tried and made more of an ordinary sniffer powerful program, since it is now possible to filter the processed data and conduct complete decoding of all packet contents.

IP Sniffer has a number of additional utilities, among which are quite good traffic monitoring, you can view the IP addresses that are most often used in the diagrams, the same can be said about the protocols. If you wish, you can work with the address determination protocol, or better known as ARM - to view it, delete various records, send responses. There is a function to help get Netbios name for a given IP address. I would like to mention the Netstat tool in IP Sniffer - it will display various kinds network connections and you will have the ability to forcibly terminate the connections you have selected, which is quite convenient.

If you need to get complete information on the network adapter used, the program will help here as well. Among other things, there is support for Spoofing of various kinds of protocols, including ARP, which means support for intercepting traffic between different hosts. IP Sniffer is able to search for DHCP servers, a built-in service for issuing information on the IP addresses you need, you can convert IP to Hostname and, accordingly, vice versa, of course, it is also possible to ping hosts and networks.

IP Sniffer does not need to be installed, can be launched from media, does not have Russian support, and has a simple interface without support for changing sniffer. In general, this is such a development in front of you, I think it will be quite useful for certain purposes. Do not forget to leave your opinions about this program, if anyone finds a use for it, we share our impressions, and do not forget that it is completely free.
Issue name: IP.Sniffer.1.99.3.6
The developer:
License: FreeWare
Language: English
The size: 7.16 MB
OS: Windows
Download:
- 7.16 MB
SmartSniff allows you to intercept network traffic and display its content in ASCII. The program captures packets passing through network adapter and displays the contents of packets in text form (protocols http, pop3, smtp, ftp) and in the form of a hex dump. To capture TCP / IP packets, SmartSniff uses the following techniques: raw sockets - RAW Sockets, WinCap Capture Driver and Microsoft Network Monitor Driver. The program supports Russian and is easy to use.
Sniffer program for capturing packets
 |
SmartSniff displays the following information: protocol name, local and remote address, local and remote port, local host, service name, data size, total size, capture time and last packet time, duration, local and remote MAC address, countries and data packet content ... The program has flexible settings, it implements the capture filter function, unpacking http responses, converting ip addresses, the utility is minimized to the system tray. SmartSniff generates packet flow report as HTML pages... The program can export TCP / IP streams.
When an ordinary user hears the term "sniffer", he immediately begins to wonder what it is and why it is needed.
We will try to explain everything in simple terms.
However, this article will be intended not only for novice users, but also for.
Definition
Sniffer Is a traffic analyzer. In turn, traffic is all information that passes through computer networks.
This analyzer looks at what information is being transmitted. To do this, you need to intercept it. In fact, this is an illegal thing, because in this way people often gain access to other people's data.
It can be compared to a train robbery - a classic plot of most Westerns.
You transfer some information to another user. She is driven by a "train", that is, a network channel.
The assholes from Bloody Joe's gang intercept the train and rob it to the bone. In our case, the information goes further, that is, attackers do not steal it in the truest sense of the word.
But let's say that this information is passwords, personal records, photographs, and the like.
Attackers can simply rewrite and photograph the whole thing. In this way, they will have access to sensitive data that you would like to hide.
Yes, you will have all this information, it will come to you.
But you will know that completely strangers know the same thing. But in the 21st century, it is information that is most valued!
In our case, this is the principle used. Certain people stop traffic, read data from it and send it on.
However, in the case of sniffers, things are not always so scary. They are used not only to gain unauthorized access to data, but also to analyze the traffic itself. it an important part works of system administrators and just administrators of various resources. It is worth talking about the application in more detail. But before that, we will touch on how these same sniffers work.
Principle of operation
In practice, sniffers can be portable devices, which are literally put on the cable and read data from it, as well as programs.
In some cases, it is just a set of instructions, that is, codes that must be entered in a specific sequence and in a specific programming environment.
In more detail, that the interception of traffic by such devices can be read in one of the following ways:
1 By installing hubs instead of switches. Basically, listening network interface can be done in other ways, but they are all ineffective.
2 By connecting a literal sniffer to the channel break. This is exactly what was discussed above - and is put small device, which reads everything that moves along the channel.
3 By installing a branch from the traffic. This branch is directed to some other device, perhaps decrypted and sent to the user.
4 An attack aimed at completely redirecting traffic to a sniffer. Of course, after the information enters the reader, it is again sent to the end user, to whom it was originally intended. v pure form!
5 By analyzing electromagnetic radiation that arise due to traffic movement. This is the most difficult and rarely used method.
Here is an example of how the second method works.
True, it is shown here that the reader is simply plugged into the cable.
In fact, it is almost impossible to do it this way.
The fact is that the end user will still notice that there is a channel break in some place.

The very principle of operation of a conventional sniffer is based on the fact that within one segment they are sent to all connected machines. Stupid enough, but so far no alternative method! And between segments, data is transmitted using switches. This is where it becomes possible to intercept information using one of the above methods.
Actually, this is called cyberattacks and hacking!
By the way, if you correctly install these same switches, you can completely protect the segment from all kinds of cyber attacks.
There are other methods of protection, which we will talk about at the very end.
Useful information:
Pay attention to the program. It is used to analyze network traffic and parse data packets using the pcap library. This significantly reduces the number of packages available for parsing, since only those packages that are supported by this library can be parsed.
Application
Of course, first of all, this concept has the application discussed above, that is, hacker attacks and illegal acquisition of user data.
But besides this, sniffers are used in other areas, and specifically, in work system administrators.
In particular, such devices or programs help to accomplish such tasks:

As you can see, the devices or programs we are considering can greatly facilitate the work of system administrators and other people who use networks. And this is all of us.
Now let's move on to the most interesting part - an overview of sniffer programs.
Above we figured out that they can be made in the form of physical devices, but in most cases special ones are used.
We will study them.
Sniffer programs
Here is a list of the most popular such programs:
CommView... The program is paid, like everyone else on our list. One minimum license costs $ 300. But the software has the richest functionality. The first thing to note is the possibility self installation rules. For example, you can make it so that (these are protocols) are completely ignored. It is also noteworthy that the program allows you to view the details and log of all forwarded packets. There is a regular version and a Wi-Fi version.

SpyNet. This is, in fact, the Trojan that we are all so tired of. But it can also be used for the noble purposes that we talked about above. The program intercepts and, which are in the traffic. There are many unusual features. For example, you can recreate the pages on the Internet that the "victim" has visited. It is noteworthy that this software is free, but it is not easy to find it.

BUTTSniffer. This is a pure sniffer that helps to analyze network packets, and not intercept other people's passwords and browser history. At least that's what the author thought. In fact, his creation is used you yourself understand why. This is a common batch program that works through command line... To get started, two files are loaded and run. Captured packets are saved on the hard disk, which is very convenient.
There are many other sniffer programs out there. For example, fsniff, WinDump, dsniff, NatasX, NetXRay, CooperSniffer, LanExplorer, Net Analyzer and many others are known. Choose any! But, in fairness, it's worth noting that CommView is the best.
So, we have sorted out what sniffers are, how they work and what they are.
Now let's move from the place of a hacker or sysadmin to the place of an ordinary user.
We are well aware that our data can be stolen. What to do to prevent this from happening? Here). It works very simply - it scans the network for all kinds of spies and reports if any are found. This is the simplest and most understandable principle that allows you to protect yourself from cyber attacks.

3 Use PromiScan. In terms of its properties and tasks, this program is very similar to AntiSniff for Windows, so choose one of them. There are many download links on the web too (here's one). It is an innovative program that allows you to remotely control computers connected to the same network. The principle of its operation is to determine the nodes that should not be on the network. Actually, these are most likely sniffers. The program detects them and signals this with an eloquent message. Very comfortably!.
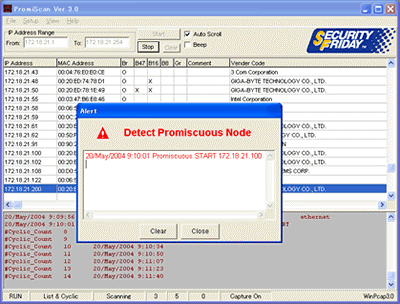
4 Use cryptography, and if deployed, a public key cryptographic system. Is it a special encryption system or electronic signature... Its "trick" is that the key is public and everyone can see it, but it is impossible to change the data, since this must be done on all computers in the network at the same time. An excellent method - like bait for a thief. In you can read about the blockchain, where such a system is used.
5 Don't download suspicious programs, don't visit suspicious sites, and so on. Everyone knows about it modern user and yet it is this path that is the main one for trojans and other dirty tricks to get into your operating system... Therefore, be very responsible about using the Internet in general!
If you have any more questions, ask them in the comments below.
We hope we were able to explain everything in a simple and understandable language.



































