Any child already at the earlier age begins to actively be interested in the toys, in which his parents play, - that is, computers, laptops, tablets, etc. often passion for such, to a certain limit for forbidden, toys over the years is only increasing. Of course, the computer opens a lot of useful opportunities for development and can give your child a good start in life, but for parents from the moment your child will make his first steps and will already be able to get to the magic screen, which are pressed by keystrokes and mysterious mouse. Life will turn into a molded nightmare. Young "researchers" are fully able to handle not only an operating system and important working documents, but at the same time, and the computer as a whole (here and the wires for which you always want to pull, and easily failing the connectors, and the system unit together with the monitor who will not be difficult to drop in the game of the game). However, the physical spectrum of problems that may occur through the fault of your kids are already a separate topic, and in this article we will restrict ourselves to considering the protection options for system and software stuffing of a home PC.
Blocking a computer
The presence in the family of a small child (and rather, too) is a problem, and there is already a double problem with the computer. To believe that yours, let only be the first steps, the child will not be interested in a bright screen and the tempting keypad buttons - at least naive, and the results from accidentally pressing the buttons and perform any spontaneous actions will not make it wait. Therefore, at the first danger of the younger generation, parents should immediately block the computer.
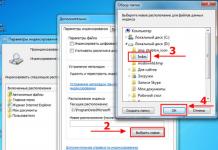
In principle, for this, it is quite enough to block the blocking function activated by pressing the keyboard combination Win + L, then it will be necessary to simply select your account and enter the password. You can also block the computer by selecting the appropriate command - in Windows Vista / 7 commands Block From the list of commands button Completion of work (Fig. 1). If desired, if none of these two ways suits you, you can create a label on the desktop that is responsible for the same operation. The label is created in the usual way, only in the field Specify the location of the object The command is entered rundll32.exe user32.dll,LockworkStation.(Fig. 2). Upon completion, it will not hurt to replace the standard label icon on a brighter, which immediately rushed to your eyes.
Fig. 1. Blocking a computer with built-in Windows tools

Fig. 2. Creating a label to block a computer
It is worth noting that the keyboard and mouse in the built-in Windows tools are not blocked. If it does not suit you, you will have to use third-party utilities, which are either developed by enthusiasts specifically to protect against playful children's pens and are free (including BLOK), or are professional solutions for blocking a computer and are offered on a commercial basis (an example is the LOCK program. MY PC).
Blok is interesting to those parents who briefly submit to a computer of small children to view cartoons (you can enable a cartoon child, and then activate the blocking, without closing the player, - Fig. 3) or, on the contrary, for a certain period there are a computer in the included state without supervision . None of the most interesting cartoon will prevent the child to use the minutes of viewing in parallel to "pointing the order to their own way", the benefit of the keyboard and the mouse will be within reach. As for situations, when parents leave the included computer at all unattended, then there are even more opportunities, and the consequences can be the most deplorable.

Fig. 3. Blocking a computer without disconnecting the monitor
Using Blok
A more reliable blocking option provides professional tools (such as Lock My PC), but for a home computer it may make sense only if you want to fully block your computer from the grown chad, which, due to excessive enthusiastic technology, your PC is no longer I am satisfied and with lust looks at your more powerful car. With the help of solutions such as a plan, you can block the computer (Fig. 4), which will be fully impossible access to any items, including the keyboard, mouse and desktop. It will be impossible to view any information on it, launch applications, access files and folders (including currently open) and even restart the computer by pressing the Ctrl + Alt + Del keyboard combination. The usual reboot even in a safe mode or power failure will not lead to removal of protection - you can unlock the computer only knowing the password.

Fig. 4. Configure computer blocking parameters in Lock My PC
Lock My PC 4.9
Developer: FSPRO LABS.
Distribution size: 1.6 MB
Work running:Windows 2000 / XP / Vista / 7/8
Distribution method: http://fspro.net/downloads.html)
Price: Personal license - 19.95 dollars; Business license - $ 29.95.
Lock My PC is a tool for blocking a computer at the moment of the user. To block, it is enough to double-click on the appropriate icon in the system tray or press a special keyboard combination. It is possible to automatically block after the expiration of the user's inactivity period. When locking, the mouse and CD / DVD drives are turned off (this will not allow you to remove compact on them) and it becomes impossible to use the main keyboard combinations: Ctrl + Alt + Del, Alt + Tab, etc. On a blocked computer, any, in any, in including created independently, images in GIF formats, JPEG, BMP and ANIMATED GIF. Unlock the computer only knowing the user password or the administrator password.
Blok 4.5.
Developer: Sergey Tsumarev
Distribution size:1.33 MB
Work running: Windows XP / 7/8
Distribution method: Freeware (http://remontnik-it.ucoz.com/load/0-0-0-1-20)
Price:is free
Blok is a utility for blocking from small children of keyboard and mouse with a monitor disable function or without on. The first option is designed to ensure safe for PC, a cartoon or fascinating animation screensavers; The second is designed to situate when the included computer turns out to be unattended for some time. Blocking is not performed instantly, but with a delay of 6 s, that in the case of blocking without disconnecting the monitor allows the parent to switch to the player window or turn on the screensaver. Lock removal is carried out by pressing the Ctrl + Alt + Del key combination.
"Freezing" system
If the child is still quite small, but has already received his own computer (for example, an old laptop), then the operating system is more reliable, using the freezer program - for example, such a recognized commercial solution as Shadow Defender, or a free utility, TOOLWIZ TIME FREEZE.
This kind of program makes a "snapshot" of almost all the hard disk with a system partition, including the system registry, and when the computer is rebooted, the Ourser is returned to its original state. This automatically means that any fatal changes made on a PC with a young experimenter (change system settings, deleting system files, dragging in an unknown direction of system folders, etc.), the computer will not be scary. Similarly, you can roll out not only unwanted changes that occurred as a result of accidental actions or user errors, but also changes in the system made by malware. At the same time, it is not necessary to perceive this kind of software products as tools for protection against malicious code, since the technology of rolling technology used in the "freezer programs" helps far from all cases, in particular, does not protect against rootkits. Therefore, the presence of an antivirus solution on a computer is strictly necessary.
"Freezing" of the system - the tool is rather radical, because after rebooting the computer, all changes made during operation in the "freezing" mode will be canceled. This is optimal when it is assumed that the you need to save documents, images and other data for the younger generation. If you want to save on your computer, all the same data is necessary, you will have to worry about it in advance and enable the folder to save them into the number of exceptions.
Use in the practice of the "Freezers" program is easy - in the simplest version, it is enough to specify the utility of the protected disk (Fig. 5) and configure the program so that the "freezing" mode automatically turned on when the system is loaded. True, it should be borne in mind that to work in this mode on a "freezed" disk there should be quite a lot of free space, since a specific disk area is temporarily (before rebooting) is reserved for a virtual area - with a lack of free space on a secure section, the program can work incorrectly . Another nuance is that when leaving the "Frost" mode (this may need to install or change, if necessary, a computer is restarted - this is not entirely convenient, but tolerant, if such manipulations are rarely produced. Also do not forget about the possibility of excluding folders (Fig. 6 and 7).

Fig. 5. Enabling the secure disk mode in Shadow Defender

Fig. 6. Determining the folders in Shadow Defender deleted during operation in the "Frost" mode

Fig. 7. Adding a folder to the exception list in Toolwiz Time Freeze
Shadow Defender 1.3.
Developer:Shadowdefender.com.
Distribution size: 2.68 MB
Work running: Windows 2000 / XP / Vista / 7/8
Distribution method: Shareware (30-day demo version - http://www.shadowdefender.com/download.html)
Price:$ 35
Shadow Defender is a simple and effective solution to protect a computer from unwanted changes, oriented on small business, educational institutions and home users. The application allows you to control the "freezing" of any of the disks, while the disk can remain in the "frozen" state after the system is rebooted. In protected mode, the system starts in the Shadow Mode virtual environment (the shadow copy that emulates the original files) and all the changes are not saved on the original section. It is possible to eliminate individual files and folders of the "frozen" disk - in such folders and file files will be automatically saved; In addition, it is allowed to exclude from the "freezing" of certain sections of the system registry. If you need to save Kakieto files or folders that are not included in the list of exceptions, in the course of working with a "frozen" disk, it suffices to use the toolage from the tab Save. For security purposes, the user is notified of the lack of free space on the "frozen" disk and protect access to the password program.
TOOLWIZ TIME FREEZE 2.2
Developer: Toolwiz Software.
Distribution size: 2.63 MB
Work running:Windows XP / VISTA / 7/8
Distribution method:freeware (http://www.toolwiz.com/downloads/)
Price: is free
Toolwiz Time Freeze is a simple program for "freezing" system. The utility can start when booting Windows immediately in the "Frost" mode; It is also possible to enable the "freezing" mode by activating the corresponding command from the menu in the system tray or from the start-up panel on the desktop. Only data on the system disk is protected from changes, some folders and / or files can be made to the list of exceptions to save changes in them in the "Frost" mode. Access to the application settings can be protected by a password.
Limiting access to system resources
With a collaborator with the child, the "freezers" of the system is quite difficult to use the computer. Why? For normal operation, every time you will have to turn off the "freezing" mode, and therefore, restart the computer, and at the end of your own work, do not forget to include protection, which is quite tedious. Another option is possible: set up a PC so that parents can normally work with a frozen system disk. The latter in practice implies a painstaking configuration of the list of panels, in which the information should be maintained. At the same time, some of the folders still will have to be protected in one way or another, so that your child in the gusts of enthusiasm can do something. In our opinion, the most correct will not "freeze" the system, but if possible, restrict access to system resources, important folders and files.
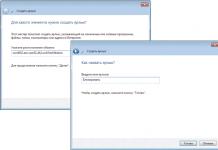
The very first in this case is to configure a separate account for a child, under which it will log in, and establish preferred system settings, as well as determine the desired set of applications. Of course, the guest profile on the computer must be disabled, and the password is installed on the administrator profile - otherwise, bypassing a similar blocking, if desired, it will not be difficult.
At the same time, it will be useful to use the parental controls embedded in Windows 7/8 and note which child programs are allowed to use (Fig. 8). It should be borne in mind that after restricting the list of available applications with built-in tools, restrict access to important system operations, such as changing settings in the control panel components (in particular, in the "System and Security" folders, "User Accounts and Family Safety", " Programs "," Network and Internet ", etc.), launch of the system registry, etc. It may not be necessary, since all such actions will automatically be banned.

Fig. 8. Setting parental control parameters for child profile in Windows 7
You can go differently through the GPedit Group Policy Editor. MS block access to those components of the operating system, the change in which is most critical and even can lead to fatal consequences. In particular, it does not prevent closing access to the control panel (or hide in it "System and Security" folders, "User Accounts and Family Security", "Programs", "Network and Internet", etc.), prohibit access to Means for editing the system registry and using the command line, set the ban on the launch of a number of applications, etc. To change the settings, you must enter Windows under the account with the administrator rights and start the Group Policy Editor by clicking the Windows + R key combination and entering the command gpedit.msc.. Then reveal a branch User configuration ® Administrative templates And adjust the settings you are interested in - for example, to completely prohibit access to the control panel (Fig. 9). Of course, "prohibit everything and the whole" - not always the most reasonable decision. It is much better to manually adjust the list of prohibited / allowed control panel elements, deleting the most dangerous items from it, but it is longer and more difficult, as you need the knowledge of the so-called canonical names of the control panel (you can familiarize yourself with the MSDN Library library - http: // MSDN .microsoft.com /).

Fig. 9. Installing the prohibition on the launch of the control panel in Windows
Other ways to configure restrictions on the change in system data are possible, but by connecting third-party applications. These can be specialized tools focused on system administrators (for example, an acceptable and relatively simple to use WinLock program), or utilities for configuring parental control (Child Control, TimeBoss, etc.).
By connecting the WinLock program, block access to important components of the operating system can be in a quarter second. So, it is easy to prohibit the use of the Windows registry editor, launch the control panel and the download in safe mode, prevent the possibility of starting the CMD.exe console, prohibit the installation and removal of programs, deprive the child the ability to block the computer and others. It may be reasonable to ban other (not having So fatal consequences, but also causing certain difficulties) operations - for example hide the properties of the screen, delete the "folder properties" item from all the Explorer menu, deny the dropping objects in the Start menu, fasten the taskbar and prohibit it setting, block the renaming of shortcuts on the desktop and T.P. (Fig. 10).

Fig. 10. Setting the locks and prohibitions in WinLock
As for the tools for setting up parental control, then the possibility of blocking access to the settings of the operating system in them, of course, more modest, but these solutions are interesting to those parents who want to protect their data at the same time and establish control over the work on the computer for the younger generation. For a Russian-speaking audience in this regard, the TimeBoss program is more interest (Fig. 11) - mainly due to the presence of a Russian-speaking interface. With it, for example, you will be able to disable the control panel and the task manager, block the launch of the system registry, as well as the change in date and time, etc. At the CHILD CONTROL application, more impressive opportunities in the Windows access control plan: You can prohibit the use of command Rows, launching the system registry, opening the control panel, changing user accounts, etc. (and taking into account the selected security level), as well as hide some discs (Fig. 12).

Fig. 11. Restricting access to system operations in TimeBoss

Fig. 12. Installation of system restrictions with the help of Child Control
WinLock 6.11
Developer: Crystal Office Systems.
Website programs: http://www.crystaloffice.com/winlock/
Distribution size: 4.96 MB
Work running:Windows 2000/2003 / XP / Vista / 7/8
Distribution method:shareware (30-day demo version - http://www.crystaloffice.com/download.html)
Price: WinLock - 23.95 dollars; WinLock Professional - $ 31.95 (in SoftKey.ru WinLock Professional - 450 rubles.)
WinLock is a convenient tool to restrict access to important system resources and user data. The program is presented in two versions: Base WinLock and Extended WinLock Professional; The capabilities of the basic version do not allow you to restrict access to webressours and use encryption.
The main purpose of WinLock is to configure user access restrictions to important system resources of the system and confidential information. The program is loaded automatically from the OS and allows you to prohibit access to the system registry and control panel, turn off the Windows hotkeys (for example, Alt + Ctrl + Del, Alt + Tab, Ctrl + Esc, etc.), hide the start menu and block the changes Task panel, etc. The utility can be used to block access to interchangeable media (CD / DVD drives, USB devices, etc.) and hiding the display of certain disks in the My Computer folder and in the Explorer, blocking the launch of specific applications (for example, you can safely Disabling download download managers), as well as files and folders with important information. It is possible to prevent access to dubious webressurours based on black and white lists (the black list is compiled by keywords) and install restrictions on the duration of the user's work on the computer. All such settings are made based on the user profile and cannot be changed without knowledge specified for the password utility.
Child Control 2013.
Developer: Salfeld Computer
Website programs: http://salfeld.com/software/ParentalControl
Distribution size:23.26 MB
Work running:Windows 2000 / XP / Vista / 7/8
Distribution method: Shareware (30-day demo version -Http: //salfeld.com/download/)
Price: $ 29.95
Child Control is perhaps one of the best solutions in the parental control setting, allowing you to restrict access to a computer in terms of introducing a limit both by time and resources used. The program also provides detailed statistics on the use of system resources and visits to websites, can guide the generated reports to the parents to the specified e-mail and is equipped with a functional for remote control.
With the help of Child Control, for each of the children, it is easy to clearly adjust access to the computer as a whole and the Internet and individual programs in particular; Block the use of individual applications and visiting unwanted Internet resources, taking into account the selected security level, pre-installed categories, keywords, official black lists of sites and white lists of URLs allowed for visiting. Possible setting time sx limits by category Websites, such as video and online games. The toolkit is provided to restrict access to the most important system components of Windows - you can block access to the system registry, command line, control panel, duty and time change component, etc. And prohibit access to personal folders and even individual disks. In order to protect the utility from hacking, the younger generation is provided to use a password access to the program and work in a hidden ("Stealth" mode.
Time Boss 3.08.
Developer: Nicekit Software.
Distribution size:1.4 MB
Work running: Windows XP / VISTA / 7/8
Distribution method:shareware (30-day demo version - http://nicekit.ru/download/timeboss.zip)
Price: Time Boss - 620 rubles; Time Boss Pro - 820 rub.
TimeBoss is a simple and convenient program for organizing parental control. The application is offered in two editions: Base Time Boss and Extended Time Boss Pro. Time Boss Pro Edition additionally provides a functionality for remote control within the local home network (you can remotely change the settings, promptly add time, etc.) and is equipped with keylogger protection (to exclude the possibility of receiving a password access to the program).
TimeBoss allows you to restrict the time of the computer's computer activity (including in games and the Internet), to determine the list of available applications (including games), enter restrictions on a number of system operations, prohibit access to individual folders and disks, as well as adjust the visits to sites during Internet surfing . The program provides control for all user-registered users and therefore, if necessary, can be used to configure different limit options for different profiles. For security reasons, it is implemented using a password access to the program, work in hidden ("Stels") mode, as well as protection from deleting an application when booting Windows in safe SAFE MODE mode.
Restricting access to personal folders
The use of different profiles with the child associated with the Windows-connected parental control in no way limits the access of your child to folders and disk files with all the consequences. Therefore, without additional protection can not do. Options for setting access restrictions to important folders can be different. The most accessible way to prevent them with access to children is to include in the properties of the corresponding objects attribute "Hidden". Thus, the folders and files will not be visible in the conductor to other users of the system, but only provided that in the properties of their parent folders, the "Do not show hidden files, folders and discs" checkbox (Fig. 13) are enabled. In principle, at first it may be quite enough to protect its data.

Fig. 13. Hiding the folder in the built-in tools of Windows
Using the built-in tools of the operating system, you can also configure access restrictions to specific folders - for example, allow only their viewing, which will prevent accidental deletion of important data. To do this, it is enough in the conductor to click on the disk, folder or file with the right mouse button, select the command from the context menu Properties, activate the tab Safety, Select a child account, and then define access to the selected object for it, configuring the required limitations (Fig. 14). Of course, you need to configure access restrictions under an account with administrator rights.

Fig. 14. Determining restrictions of access to the folder in the built-in Windows tools
In this way, you can even completely prohibit access to individual folders, but the folders themselves will remain in the system visible if the "hidden" attribute will not be set to the displays the display of hidden folders and files. Unfortunately, the folders will be covered with the use of built-in Windows folders will be visible in file managers (FAR, Total Commander, etc.) that do not use a standard dialog to display files and folders. Therefore, such a concealment is not suitable for everyone.
To organize more efficient protection of those folders that you would like to stay away from curious children's eyes, you can go to another way - use a specialized solution, such as the Free Hide Folder utility or Protected Folder. Fully hide individual folders with their help with their help simpler simple - just drag the corresponding folder from the conductor into the utility window either directly in the Utility window add this folder to the number of protected (Fig. 15 and 16). Hidden with the connection of the free FREE Hide Folder utility folders will not be visible in Windows Explorer Even when the "Show hidden files, folders and disks" option is enabled, however, if your child is hidden enough and you will forget to prohibit use in the Children's Profile of File Managers (Far, Total Commander etc.), then to circumvent the defense you have established will not be difficult. Commercial program Protected Folder provides a more reliable level of concealment - the folders protected in it will also be invisible in file managers; Access to them without knowledge master password is impossible. It is worth noting that it is possible to protect confidential folders using the above-mentioned Parental Control utilities and TimeBoss.

Fig. 15. Hide folders in FREE Hide Folder

Fig. 16. Installation of protection to the folder in Protected Folder

Fig. 17. Hiding important data in the CHILD CONTROL program
Such a data hiding will help protect them from unauthorized access and random damage or deletion in many cases, although the chances of accessing folders in a young hacker have, if you do not take care of blocking the capabilities of the system booting from an optical drive or flash drive and installing a password on the BIOS. In addition, the theoretically bypassed protection can be if you remove the disk and connect it to another computer. True, if you have any kind of qualifications, parents hardly already make sense to fight with software.
PROTECTED FOLDER 1.2.
Developer: Iobit.
Distribution size:3.4 MB
Work running:Windows XP / VISTA / 7/8
Distribution method:shareware (demo version 20 launches - http://ru.iobit.com/downloads/pf-setup.exe)
Price:600 rub.
Protected Folder is a convenient program to protect files and folders from unauthorized access by completely hiding or restricting data access. In terms of access restrictions, it is possible to install a ban on reading (the files will remain visible, but they can not be launched, copying and read) or prohibit an entry (cannot be moved, deleted and modified). Hidden data invisible in Windows Explorer and in file managers. Access to the program is protected by master password. The functionality is provided to configure exceptions - by default, a number of system folders and files are included in the list of exceptions, since the access limit to them leads to incorrect operation of the system.
FREE HIDE FOLDER 3.0
Developer: Cleanerersoft Software.
Distribution size: 875 KB
Work running: Windows 9X / ME / NT / 2000 / XP / 2003 / Vista / 7/8
Distribution method: Freeware (http://www.cleanerersoft.com/download/fhfsetup.exe)
Price:is free
Free Hide Folder is a simple and compact utility for hiding personal folders. Protected folders become completely invisible to Windows Explorer, even when the "Show hidden files, folders and discs" option is enabled, but will be displayed in other applications, such as FAR, Total Commander, etc. Access to the program is closed by a password master.
As everyone is well known, with children there are always enough problems, and if there are also a computer at home available, then you will not have to miss you. You will probably master the mass of the methods of fixing the wires, hiding from the children's eye block with a valuable filling, strengthening the monitor, and then go to the study of the most different software (for example, what was considered in the article) to limit the access to the younger generation to the computer, operating system, as well as important folders and files. However, if a real computer genius grows in the family, then even after the protection of everything and all of you can hardly be resting on the laurels. In this case, it will only be recognized as a defeat that, maybe for the better, because then it will immediately become clear that computers are the true vocation of your child.