Tickets AIS.
1administering. System and Network Administration ratio 2
2Administering. Network administration 4.
3Administering. System administration 5.
4Administering. Managing IT services. Problems and prospects 7
5ITSM, solved questions, the need to use 9
6Itil, connection with ITSM 10
7P. ITIL and possible problems 11
8Knigi ITIL 12 library
9Itil, provision of services 13
10itil, support services 15
11This books ITIL. Certification 16.
12 Standards, Theories and Methodologies 17
13ItPM, composition, distinction 18
14ItPM for enterprises. IRM - ITPM \u200b\u200bIdea Explorer 19
15 Architecture Tivolli Enterprise 20
16TMF (Tivoli Management Framework) 21
17tivoli. The main disciplines of management and control applications. Deploying on 22.
18tivoli. The main disciplines of management and control applications. Ensuring the availability of networks and systems 23
19tivoli. The main disciplines of management and control applications. Automation of processes. Safety information resources 24
20tivoli. SERVICE Desk (3 applications) 25
21tivoli. Information Infrastructure Management (GEM), Application Management 26
Administration. System and Network Administration Ratio
AdministrationPurpose
The history of system administration has several decades. In connection with the dominant architecture of the "host terminal" model, the administrative organization was also centralized. In the 90s, the turbulent distribution of the client-server architecture led to fundamental changes: instead of observing a homogeneous environment, the administrator needed to solve many tasks: accounting for resource distribution, license control, load redistribution, etc.
From the point of view of solved tasks, when mainframes prevailed, their administration could be attributed to the category system Administration. With the advent of distributed architecture, the management tasks were limited to the supervision of the functioning of individual components. System administration includes:
Solution of problem situations
Resource management
Configuration management
Performance control
Data management
Network administrationit originated when administrators had the ability to control the entire network. For a while, network administration began to be considered as the main concern for IP administrators, which did not quite correspond to the logic of the functioning of the kit. The network plays the role of just infrastructure. Network administration includes:
Control over the operation of network equipment
Managing network functioning as a whole
When the number of distributed applications exceeded the threshold value, the process of integrating system and network administration was inevitable. Network administration began to be considered as a component of system administration, and the network is as one of the managed resources.
Administration. Network administration
Administration- These are the control procedures that regulate some processes or their part. Such processes include work planning, building, operation and support for efficient IT infrastructure integrated into the overall architecture of the information system. Purposeadministration is the achievement of such parameters of the operation of the IP, which would suit the needs of users.
Network administration includes:
Control over the operation of network equipment- Monitor individual network devices, setting up and changed their configuration, troubleshooting. Also called reactive control.
Managing network functioning as a whole- Monitoring network traffic, identifying trends of its change and analysis of events to preempt network problems. This uses a single network presentation in order to make changes to the network, accounting for network resources, management of IP addresses, package filtering. Also called preventive administration.
The most common architecture is the Manager agent. The manager is run on the control console, constantly interacts with agents on network devices. Agents collect local data on the network device operation parameters.
A three-level scheme is now applied: part of the control is delegated to the most important network nodes. Program managers are installed in the nodes, which through their own network of agents manage the operation of devices, and themselves are agents of the central manager. Local and central managers interact only if necessary.
Network software industry is divided into three parts:
Network Management Platforms
Managers of network hardware manufacturers
Third parties aimed at solving narrow network administration tasks
Course project
Computer network administration on the example of LAN STK
Introduction
Computer network management - Performing a variety of features necessary for control, planning, isolation, implementation, coordination and monitoring computer network resources. As a rule, this term applies to large-scale computer networks, communication networks, designating support and administration of these networks at the top level. This is the main purpose of administering networks. Computer network management includes execution of features such as initial network planning, frequency distribution, distance routes predestination to support load balancing, cryptographic key distribution, configuration management, fault tolerance, safety, performance and accounting information. The goal of the course project is to create an electronic reference book on "Creating an electronic reference book on the topic" Administering a computer network on the example of a locally computing network of the Solimsk technological college ". The following tasks flow from the purposes: · search and systematization of information on the topic of the project project; · overview of programs for creating an electronic reference book; · acquaintance with the program interface; · drawing up the structure of the electronic reference book. 1. Theoretical part
.1 main network administration functions
The International Organization for Standardization described the FCAPS model in which key network administration and network management functions are reflected: · (F) Fault Management / Failure Management · (C) Configuration Management / Configuration Management · Accounting Management / Network Accounting · (P) Performance Management / Performance Management · (S) Security Management / Security Management Objective management tasks - identifying, defining and eliminating the consequences of failures and failures in the network. The configuration management consists in configuring network components, including their location, network addresses and identifiers, managing network operating systems, maintaining network schemes: also these functions are used to naming objects. Accounting for networking includes registration and management of used resources and devices. This feature operates with such concepts as use time and fee for resources. Performance management is used to submit a real-time network work statistics, minimizing congestion and bottlenecks, identifying trends and resource planning for future needs. Security Management - includes access control, saving data integrity and journaling. The function includes the authentication procedure, privilege checking, support for encryption keys, managing powers. To the same group, you can include important password management mechanisms, external access, connections to other networks. Specific sets of these functions to one degree or another are implemented in the development products of administration and management tools. Exists a large number of Protocols providing network management and network devices. The most famous among them are: SNMP, WMI, CMIP, WBEM, Common Information Model, Transaction Language 1, Netconf and Java Management Extensions. Some network management systems: .2 Responsibilities of the system administrator network Administrator Malicious Program To perform the functions assigned to it, the network administrator performs the following duties: · Supports uninterrupted operation of a local computer network. · Carries out support for the functioning of the computer network databases. · Provides data integrity, protection of them from unauthorized access, regulates network user access rights to computer network resources. · Performs installed backup data requirements of a computer network. · Uses standard and special means of registration and accounting access to computer network information. · Applies optimal programming methods in order to fully use the means and features of computer equipment. · Magazines needed for the normal functioning of the computer network. · Conducts training computer network users. · Determines the ability to use ready-made programs issued by other organizations, implements their implementation. · Participates in the development of source data and setting tasks to upgrade a computer network. · Considers at the coordination stage, the project documentation for improving access control systems for compliance with the requirements of the Guidelines and Technical Occasion, if necessary, makes appropriate adjustments. · Provides information security of a computer network. · Develops the rules of computer network operation, determines the authority of the computer network users to access the computer network resources, performs administrative support (setting, monitoring and prompt response to incoming signals of established access rules, analysis of security logging logs, etc.). · Participates in the development of technology information security An employer providing for the procedure for the interaction of the employer's units on security issues during the operation of the computer network and the modernization of its software and hardware. · Prevents unauthorized modifications software, add new features, unauthorized access to information, equipment and other general resources of the computer network. · Performs support and, if necessary, the improvement of implemented software According to information protection. · Develops programs for information protection of a computer network and network applications. · Develops methods and methods for organizing access to computer network users to computer network resources. · Informs employees of the organization about vulnerable places of computer network, possible ways of unauthorized access and exposure to a computer network, well-known computer viruses. .3 System planning
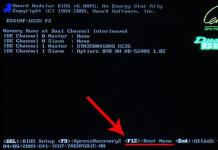
Before installing the system, you need to know the answers to the following questions: · What information processing tasks is solved by the information system? · How many computers are used in the information system? · How to build a network (topology, routing, etc.)? · What is the security policy in the information system? etc. It is necessary to set the criteria for accepting new systems and carry out the appropriate tests before their acceptance. For this, the following items are considered: · requirements for performance and load capacity of computers; · preparation of recovery procedures and restarting systems after failures, as well as action plans in extreme situations; · preparation and testing of everyday operating procedures in accordance with the specified standards; · note that installation new system will not have detrimental consequences for functioning systems, especially at the moments of the peak load on processors (for example, at the end of the month); · preparation of personnel to the use of new systems. .4 remote administration programs
Programs or functions of operating systems that allow you to obtain remote access to the computer via the Internet or LAN and control and administer the remote computer in real time. Remote administration programs provide almost complete control over remote computer: They make it possible to remotely manage the computer's desktop, the ability to copy or delete files, launch applications, etc. There are many implementations of remote administration programs. All implementations differ over the interface and used protocols. The interface may be visual or console. Some of the most popular and common programs are, for example, the Windows Remote Desktop Services component with a client. Remote Desktop Connection, Radmin, DameWare, Putty, VNC, Ultravnc, Apple Remote Desktop, Hamachi, TeamViewer, Remote Office Manager, etc. Actually, the remote administration protocols are used for the purpose of transferring and output commands: RDP, VNC, X11, Telnet, RLOGIN, RFB, ARD, ICA, ALP and Own. To encrypt traffic in remote administration programs, SSH, SSL, TLS, etc. protocols are used. .5 tasks and objectives of network administration
Modern corporate information systems are always distributed systems by their nature. User Work Stations, Application Servers, Database Servers and Other Network Nodes are distributed over a large area. In a large company, offices and platforms are connected by various types of communications using various technologies and network devices. The main task of the network administrator is to ensure reliable, uninterrupted, productive and safe operation of the whole of this complex system. The network is a set of software, hardware and communication tools that ensure the effective distribution of computing resources. All networks are divided into 3 categories: · local networks (LAN, Local Area Network); · city Networks (MAN, Metropolitan Area Network.).
Global networks allow you to organize interaction between the subscribers at large distances. These networks operate at relatively low speeds and can make significant delays in the transmission of information. The length of global networks can be thousands of kilometers. Therefore, they are somehow integrated with the scale of the scale of the country. Urban networks allow you to interact on the territorialities of smaller dimensions and operate at speeds from medium to high. They slowly slow down the transmission of data than global, but cannot provide high-speed interaction at large distances. The length of urban networks is located from several kilometers to tens and hundreds of kilometers. Local networks provide the highest information exchange rate between computers. A typical local network occupies space into one building. Length local networks It is about one kilometer. Their main purpose is to combine users (usually one company or organization) for collaboration. Data transmission mechanisms in local and global networks differ significantly. Global networks are focused on the connection - prior to the start of data transmission between subscribers the connection is established (session). In local networks, methods that do not require pre-connection is used, the data packet is sent without confirming the readiness of the recipient to the exchange. In addition to the difference in the data rate, there are other differences between these categories of networks. In local networks, each computer has a network adapter that connects it to the transmission medium. Urban networks contain active commuting devices, and global networks usually consist of groups of powerful packet routers, combined communication channels. In addition, the network can be private or shared networks. Network infrastructure is built from various components that can be deprived in the following levels: · cable system and communications; · active network equipment; · network protocols; · network services; · network applications. Each of these levels may consist of various sublevels and components. For example, cable systems can be built on the basis of a coaxial cable ("thick" or thin "), twisted pair (shielded and unshielded), fiber. Active network equipment includes such types of devices as repeaters ( repeitors), bridges, hubs, switches, routers. A rich set can be used in the corporate network. network Protocols: TCP / IP, SPX / IPX, NetBeui, AppleTalk, etc. The basis of the network is the so-called network service (or services). The basic set of network services of any corporate network consists of the following services: 1.network Infrastructure Services DNS, DHCP, WINS; 2.file and Print Services; .directory Services (for example, Novell NDS., MS Active Directory); .messaging services; .access services to databases. Most upper level Network functioning - network applications. The network allows you to easily interact with each other. Different types of computer systems thanks to standardized data transfer methodsthat allow you to hide from the user all the variety of networks and machines. All devices running on the same network must communicate in the same language - to transmit data in accordance with the well-known algorithm in the format that will be understood by other devices. Standards - a key factor when combining networks. For a more strict description of the network, special models have been developed. Currently, generally accepted models are the OSI model (Open System InterConnection) and the TCP / IP model (or model Darpa.). Both models will be discussed in this section below. Before determining the tasks of network administration in a complex distributed corporate network, we formulate the definition of the term "corporate network" (COP). The word "Corporation" means the association of enterprises working under centralized management and decisive common tasks. The corporation is a complex, multidisciplinary structure and as a result of this has a distributed hierarchical control system. In addition, enterprises, branches and administrative offices included in the corporation are usually located at sufficient distance from each other. For centralized management, such an association of enterprises uses a corporate network. The main task of the COP is to ensure the transfer of information between various applications used in the organization. The application means the software that is directly needed to the user, for example, an accounting program, text processing program, email, etc. The corporate network allows you to interact applications, often located in geographically different areas, and provides access to remote users. In fig. 1.1. The generalized functional scheme of the corporate network is shown. The obligatory component of the corporate network is local networks related to each other. In general, the COP consists of various offices united by networks. They can be global (WAN) or urban (MAN). Fig. 1.1. Generalized CS scheme Network administration tasks in a complex distributed CS: Network planning. Despite the fact that planning and installation large networks Usually, specialized integrators companies are engaged, the network administrator often have to plan certain changes in the network structure - adding new jobs, adding or deleting network protocols, adding or deleting network services, installing servers, splitting the network to segments, etc. These work should be carefully planned so that new devices, nodes or protocols are included in the network or are excluded from it without disrupting the integrity of the network, without reducing performance, without violating the infrastructure of the network protocols, services and applications. 1.Installing and configuring network nodes (active network equipment devices, personal computers, servers, communications). These works may include - replacing the network adapter in the PC with the appropriate computer settings, transferring the network node (PC, server, active equipment) to another subnet with the appropriate changes in the node network parameters, add or replacing the network printer with the appropriate job setting. 2.Installing and configuring network protocols. This task includes the execution of such works - planning and configuring the basic network protocols of the corporate network, testing the operation of network protocols, determining the optimal configurations of the protocols. 3.Installing and configuring network services. The corporate network may contain a large set of network services. Briefly list the main tasks of network administration tasks: · installing and configuring network infrastructure services (DNS, DHCP, WINS, Routing Services, Remote Access and Virtual Networks); · installing and configuring files and print services that currently make up a significant part of all network services; · directory Services Administration (Novell NDS., Microsoft Active Directory) forming the basis corporate system security and network access controls; · administer Messaging Services (Email Systems); · administer access to database services. 4.Troubleshooting. The network administrator must be able to detect a wide range of faults - from a faulty network adapter on workstation User to the failures of individual ports of switches and routers, as well as incorrect settings for network protocols and services. 5.Search for narrow network sites and improve network efficiency. The network administration task includes the analysis of the network operation and the determination of the most bottlenecks that require either replacement of network equipment, or upgrading jobs, or changes in the configuration of individual network segments. 6.Monitoring network nodes. Monitoring network nodes includes monitoring the operation of network nodes and the correctness of the functions assigned to these nodes. 7.Monitor network traffic. Network traffic monitoring allows you to detect and eliminate various types of problems: high loading of individual network segments, excessive loading of individual network devices, malfunctions for network adapters or network devices, unwanted activity or attacks of intruders (spread of viruses, hacker attacks, etc.). 8.Ensuring data protection. Data protection includes a large set of various tasks: backup and data recovery, development and implementation policies of user accounts and network services (password complex requirements, password change frequency), building secure communications (application of IPsec protocol, building virtual private networks, wireless protection), planning, implementation and infrastructure maintenance open keys (PKI). .6 Security Administration
Security Administration Includes the dissemination of information necessary for the operations and safety mechanisms, as well as the collection and analysis of information about their functioning. Examples include the distribution of cryptographic keys, setting the values \u200b\u200bof protection parameters, maintaining a registration journal, and the like. Conceptual administration basis is the security management information base. The base may not exist as a single (distributed) storage, but each of the terminal systems should have the information necessary for the implementation of the elected security policy. According to the recommendations of the X.800, the efforts of the Security Administrator must be distributed in three areas: administration of the information system as a whole; Security Administration; Administration of safety mechanisms. Among actions, we note ensuring the relevance of security policies, interaction with other administrative services, responding to occurring events, audit and secure restoration. Administration of security services includes the definition of protected objects, the development of the safety mechanisms (if there is alternatives), combining mechanisms to implement services, interaction with other administrators to ensure coordinated work. The obligations of the administrator of safety mechanisms are determined by the list of mechanisms involved. The typical list is: · key management(generation and distribution); · encryption management(installation and synchronization of cryptoparameters); · administration of access control(distribution of information, · necessary to manage passwords, access lists, etc.); · authentication Management(distribution of information necessary for authentication - passwords, keys, etc.); · control of traffic addition(Developing and maintaining rules specifying the characteristics of complementary messages - the frequency of shipment, size, etc.); · routing management(allocation of trusted paths); · notarization management(Dissemination of information on notarial services, administering these services). So Administration of security tools in distributed IP has many features compared to centralized systems. 1.7 Malware Protection Automatic update - Modern operating systems are very complex software products, and hackers sometimes manage to find vulnerabilities in them, allowing you to get control of the computer. When it becomes known to programmers from Microsoft, the system update is immediately issued, liquidating vulnerability. Timely windows Update 7 will protect against hacking using any of the well-known vulnerabilities. DEFENDER - not just a system scanner like other similar free programs. It includes a number of security modules that track suspicious changes in certain system segments in real time. Also, the program allows you to quickly delete installed applications ActiveX. Using Microsoft Spynet network access, you have the ability to send suspicious objects to Microsoft to determine its possible accessory to Spyware. Operation with media and their protection To use the control mode for the use of external media in Windows 7, the administrator must use group (local) policies. Using group policies, the administrator can specify specific devices that are allowed on this computer. This can be done in several ways: ) Access using the device ID Suppose that the order employee has allocated a flash drive A, but from the house, it can bring another flash drive V. Means of group policies in Windows 7, it can be done so that the flash drive will work, and when the flash drive is turned on, the employee will receive Notification that he violates the security policy. ) Encryption of interchangeable media Encrypting media in Windows 7 can be made in several ways. The easiest way is the USB disk encryption in the event that it is formatted under NTFS. In this case, encryption is carried out similarly to the encryption of the hard disk. However, some of the Encryption Group Policy Rules can be used specifically to control replaceable media. For example, using Provide The Unique Identifiers for Your Organization, you can specify the unique name of the organization, and then use this field to control replaceable media. 3) DENY WRITE ACCESS TO REMOVAL DRIVES NOT PROTECTED BITLOCKER Using this policy rule, you can prohibit the recording on interchangeable discs that are not protected by BitLocker. In this case, all interchangeable discs that are not protected BitLocker will be read only. If the "Deny Write Access to Devices Configured in Another Organization" option is selected, in which case the record will be available only on interchangeable discs belonging to your organization. Verification is performed in two identification fields defined in accordance with the GRUPP RULES "PROVIDE THE UNIQUE Identifiers for Your Organization". .8 Control
The concept of data protection computer includes both the development and implementation of appropriate protection methods and their constant use. The introduction of data protection begins with the order of the manager and ends with the practical application of protection methods. The need for information protection is due to the centralization of economic information processing at computing centers of collective use, facilitating access to data thanks to communications with more powerful computers and more strict state regulation of secrecy, as well as market relations, when needed to maintain a commercial secret. The functioning of the ASOA is based on the creation of information banks. Tools allow this data to be made available for everyone who has access to a common telephone line. An increasingly growing data concentration along with their accessibility thanks to communication lines increases the need to protect information, and if it takes into account that enterprises are striving for the preservation of commercial secrets, the data protection is extremely necessary. Powerful computers create conditions for the growth of unauthorized access to computer resources, allow complicated information processing procedures. For example, the use of database database management systems creates such capabilities that within a few minutes the actions are provided for which months will be necessary for designing, encoding, implementation, testing and processing information without using the database. The creation of a democratic legal state determines the need for a guarantee of the rights of inviolability of a person when processing on computer information about personal life, correspondence, family income, etc. To implement the warning functions of financial and economic control and audit, data protection avoids abuses of persons having access to computer databases. Practice shows that under conditions of assets of the embezzlement of values \u200b\u200bare carried out with the participation of accountants and employees of computing centers that are engaged in the processing of economic information. The main goal of protecting computer data is the prevention of phenomena negatively affecting the results of the management. Destruction of information is the unauthorized destruction of information resources to conceal the facts of theft of values. This concerns accounting and economic information on settlements with employees of the enterprise, suppliers, on the use of material values, cash, etc. Theft of data - the embezzlement of information from the computer can be carried out without the destruction of databases. In particular, such information is the codes of an employee of the enterprise, inventory and material values, production operations. Having indicated codes at the stage of preparation of data and processing them on a computer, dishonest persons can oversee the earnings to individual workers, to write off the production costs precious metals and scarce materials, thus excessive to resign them. Changing data - intentional data distortion - includes erasing and replacement of records, the use of incorrect code designations in accounting of money and material values, etc. For example, the code of the tablet number of the disadvantaged employee is saved in the database and are used to accrue wages Facular face with the subsequent transfer of money to a special account in Sberbank. Incorrect use of ACSA funds and computer resources are often used to handle information for other enterprises on the so-called cooperative basis, when the employees of the computing center receive payment of services for salary accrual, consideration of material values \u200b\u200band funds personally, bypassing the enterprise to which the equipment has a computing equipment Technique. As a result of this operation, depreciation of the computer and other technical means, the maintenance of the premises, the energy costs are not compensated by the Obserner of the Computing Center. Data protection is carried out by a special official - an administrator for the protection of information. Its function includes the provision of physical and logical protection of information resources. Physical protection covers technical means, an computer room, communication lines and remote terminals, logical - concerns the data themselves, as well as application programs and software operating systems. The functions of the special administrator provide responsibility for the confidentiality of the data. Without personal responsibility, it is difficult to enter, implement and monitor the program of information security, which includes: the responsibility of employees for the safety of information files; bringing to the guidance of data protection cases; Fight against violators of file protection. Technical protection tools are used by the Security Administrator to protect both the computing installations themselves and data or programs within these settings. Data protection software are used in real-time operating conditions with AUM special programs. Security tools can be embedded in system software packages in application systems. In addition, the identification of specific needs may be elected such means of protection that best suggest solving these problems. The data protection verification program is by simulating with tests of different distortion options or data embezzlement in order to make illegal actions. Although tests for verifying data protection cannot cover all possible abuse options, testing is still the most radical means of creating and operating data protection programs. The auditor and the auditor of the current and future generations are not similar to their predecessors. Both the function of the documentary auditor, and the idea of \u200b\u200bit quickly change with the change in the concepts of the management of the national economy and the role in it financial and economic control. Therefore, the method of protecting data in the ASOs will be constantly improved as new generations of computer and the development of data management systems are detected. Consequently, controlling the protection of data of the computer creates the necessary prerequisites for the avoidance of information distortion at the preparation, processing and storage stages in order to prevent employee abuses and ensure the safety of values. .9 programs for creating an electronic reference book
The more reference material at the disposal of the user, the calmer he must feel. But the abundance of materials generates another problem: how to provide the user with fast and convenient access to a specific topic, to a specific term, etc. Creation of electronic documentation has been based on a hypertext technology for a long time. One of its most important advantages is the availability of interactive references that allow the reader to move between themes almost in any arbitrary order. "Almost", because in fact, possible transitions are determined by the navigation structure of the document proposed by its creator. In addition, certain features in working with the document are due to the specifics of a particular hypertext format. Currently, about a dozen different formats, including PDF (RICH TEXT FORMAT), DOC (Document Word) and Winhelp, and Winhelp, and Winhelp, and Winhelp, and Winhelp (Windows Help), as well as a whole family of hypertext marking languages \u200b\u200bare applied to hypertext documents. From which you can read HTML (HYPERTEXT Markup Language) and XML (Extensible Markup Language). This should also add specialized CHM format (Compiled HTML). However, not all of the existing formats are suitable for creating reference books. Causes Different: Some formats do not provide an acceptable compactness of the final document, others do not have sufficient functionality and expressiveness, the third requires installation on computers of users of additional (and expensive) software. Fig. 1.2. File help system in pdf format Access to the directory can be implemented in several ways. The most common one is an explicit call through the appropriate command menu command, but use is also possible. special buttons on the toolbar or call through context menu Specific object icon. So, in order for the electronic document format to be suitable for creating a reference book, it (format) must have the following properties: · ensure the acceptable compactness of the final document; · have sufficient functionality (in particular, support full-text search); · maintain the possibility of presenting multimedia information (graphics, video, sound); · do not require installation on computers of users of additional software; · it is easy to integrate with the program code of the application being created. For applications developed under Windows, today the most of their listed requirements are answered by three formats: WinHelp, HTML, HTML HELP (CHM). During the time that has passed since the appearance of Help Workshop (and then - HTML Help Workshop), third-party developers have suggested a lot of tools intended for the creation of reference books. However, all of them to generate output files (.hlp I.Chm) use engines from Help Workshop and HTML Help Workshop. In some products, only compilers of the appropriate formats are involved, in other directories developer provided full access to the Help Workshop and HTML Help Workshop interface. Thus, when the question arises about the choice of the most suitable tool, it makes sense to take into account the following factors: · What weekend formats of reference books it supports; · How fully it uses the opportunities that the reference format provides; · How comfortable means of managing project parameters; · Whether there is a means of testing hypertext references as part of the tool; · Lee allows the tool to work with source data formats (RTF - for WinHelp and HTML - for HTML HELP); · Saskolko is conveniently implemented by interaction with additional tools necessary for the preparation of multimedia materials; · What is the degree (or the ability) of integration with the application development environment for which the directory is created. When creating reference books in Russian, an essential factor is also how correctly the tool works with Cyrillic (although WinHelp and HTML HELP formats themselves do not impose any restrictions in this regard.) Help and Manual. The estimated version of the program is located on the developer's website, EC Software, at www.helpandmanual.com. The estimated version is operational within 14 days. There is one more restriction: when generating a reference book in HTML Help format, some hypertext links are replaced by references to the developer's website. With this package, you can get a reference book in three formats: WinHelp, HTML Help and Webhelp (Helpand Manual developers are named Brouser Based Help). In addition, it is possible to export a reference to the PDF file and to the format file. text editor Word (.doc or.rtf). Finally, the Help and Manual package is able to create e-books (Electronic Book). Such a book looks very similar to HTML HELP format, but is an independent Windows application (EXE file). The format of the electronic book has one significant disadvantage - it is not very compact (but it is quite suitable for the distribution of additional training materials on CDs). The Helpand Manual package uses for generating reference books in WinHelp and HTML Help compilers from Microsoft, but direct access to the Help Workshop interface and HTML Help Workshop does not have a directories. It should be noted that the Help Workshop program includes the distribution, but HTML Help Workshop is supposed to be obtained on the website of EC Software. If this tool is already installed on the computer, it is necessary to specify its location. Helpand Manual package is able to decompile reference files (.hlp I.Chm) and create a new project based on them. When creating a Russian-language reference book in WinHelp format no additional settings Not required. Before generating the CHM file, you must specify the language used. Also, on the company's website you can get the Russian dictionary connected to Help and Manual to check the spell spelling of the sections. MIF2GO.Go is not an independent application, but a plug-in that can only work with Adobe Framemaker package. "This is a program for layouts focused on creating a large amount of documents that have a complex structure. It implements funds for automatic numbering Tables and illustrations, construction of table contents and pointers. In addition, it supports cross-references and hypertext links, allows you to tie graphics to text paragraphs and much more. You can divide the document to the chapters, collect chapters in the book, and Framemaker will automatically update the page numbers and links regardless of how the pages, chapters or partitions are rearranged. For storage, Framemaker uses its own file format (.fm I.Book), but the program has tools that allow you to export files to PDF and HTML formats. It should also be noted, the STRAMEMAKER program was originally created to prepare technical descriptions Arms systems (in particular, aviation technology), as well as layouts of texts that require frequent updates (what is the documentation for software). The MiF2GO package was developed by OMNI Systems, and for individual categories of users (not corporate technical writers, students studying Framemaker, and some others) applies to free. The company's website (www.omsys.com) also has a demo version of the package. It is full-featured, except that when generating a reference book, individual text fragments are replaced by randomly rows from Lewis Kerolla "Jabberwocky" .go allows you to create reference books in five formats: WinHelp, HTML Help, Omnihelp (own cross-platform format of the reference system of OMNI Systems similar to the Webhelp format), Oracle Help and Javahelp. To generate output files in the listed formats, the relevant compilers are required on the computer, which are not included in the MIF2GO distribution and must be installed separately. Actually, to connect MiF2GO to Framemaker installation as such is not required. It is enough to copy the files from the distribution to the folders specified in the installation instructions. As source data for creating WinHelp and HTML HTML Help, the Mif2Go program uses files in RTF and HTML formats. However, before you are received from your own Framemaker files (.fm I.Book), there must be a multi-step conversion process. Robohelp.- This is a whole family of products manufactured by Ehelp Corporation (www.ehelp.com). Three options are possible. Enterprise. This option includes the only RoboHelp Enterprise product that allows you to create a reference system in the format of the same name. Its significant difference from all formats discussed above is that it assumes the presence of a server and client part of the reference system. Server software based on using Microsoft Server (Internet Information Server) from Microsoft allows you to track the actions of the user operating with the reference system. Thanks to this, the developer can get very valuable statistical data on the interests of users. The format of the client part of the reference is similar to the WebHelp format. Professional. This option includes a set of tools under the general name of Robohelp Office. The set includes: · Robohelp HTML - application designed to create reference systems based on hTML language and allowing you to generate reference books in Webhelp formats, Microsoft HTML Help, Javahelp and Oracle Help for Java; · Robohelp Classic - an application specializing in the preparation of reference books in WinHelp format, including in a modified WinHelp 2000 format; · Robohelp Tools - Additional service applications designed to facilitate the work of the directory author (including Software Video Camera - an application that allows you to "remove" a sound video about working with the application). Standart. This is a lightweight version of Robohelp Office, which includes three tools: · Robohelp for Microsoft HTML HELP - application for the development of HTML HELP reference systems; · Robohelp for WinHelp - application for developing reference systems in WinHelp format; · Robohelp for Word is an application that allows you to create reference books in all standard formats (Webhelp, Microsoft HTML Help, Javahelp), but with one limitation: as editor of the sections (including HTML files) can only be used with it. Microsoft Word..
To work with source data formats (RTF - for WinHelp and HTML - for HTML Help), the default Microsoft Word uses the default, however, to create a directory partitions, it connects its own templates, largely automating the editing process. Word cannot be considered an ideal tool for creating files In RTF and HTML formats, since the output files contain excess tags. But if there is no alternative to work with RTF, then to prepare partitions in Robohelp HTML, it is fashionable to be fashionable to connect any HTML editor. When developing using the Robohelp HTML application, the Cyrillic is not correctly displayed. Because Initially, the RoboHelp Office does not provide support for the Russian language. At the same time, Robohelp practically does not change the parameters of the RTF file created in Word. Therefore, when generating a reference book in WinHelp format, language problems are rather rare. When creating a reference system in HTML Help format, problems with the correct display of Cyrillic (at the directory development phase) are more likely. This problem can be solved in several ways, including by connecting to the Robohelp HTML external HTML editor.
At the beginning of its history, all computers were autonomous and worked separately from each other. With an increase in the number of cars, it was necessary to jointly work them. In particular, it concerned the work of users over one document. The solution to such a problem was the use of global and local networks. The construction of networks caused the need to manage this process, as well as perform various tasks. Network administration took these functions.
Basic network administration functions
According to international standards, the network administration has the following functions:
- Failure management. This includes the search, the correct definition and elimination of all problems and failures in the specific network.
- Configuration management. We are talking about the configuration of system components, including their location, network addresses, network operating systems, etc.
- Accounting for networking. Computing network administration includes registration and subsequent control over the resources used and network devices.
- Performance management. We are talking about providing statistical information about the operation of the network for the specified period of time. This is done in order to minimize the cost of resources and energy, as well as for the purpose of planning resources for future needs.
- Security management. The function is responsible for access control and saving the integrity of all data.

Different sets of these functions are embodied in products for network developers.
Duties of the system administrator
Administration computer networks It occurs under the control and management of the system administrator, before which the following tasks cost:
Checking the database performance.
- Control over the uninterrupted operation of local networks.
- Protection of data and ensuring their integrity.
- Network protection from illegal access.
- Adjusting the license network access rights to network resources.
- information.
- Using optimal programming methods to fully use available tools and network resources.
- Maintain special journals for networking.
- Implementation of user training users.
- Control over the software used.
- Control over the improvement of a local computer network.
- Development of network access rights.
- Suspending the illegal modification of the software software.

The system administrator is also responsible for informing the employees of a particular enterprise or organization of weak places of the network administration system and possible ways of illegal access to it.
Features and criteria for planning systems
Before installing a computer network you need to find answers to the following questions:
- What tasks will decide and what functions will system?
- How will the computer network be built? (its type, routing, etc.)
- How many computers will be present in the network?
- What programs to administer network will be used?
- What is the security policy of an organization where the system will be installed, etc.

Answers to these questions will allow you to create a criteria system for a particular computer network, where the following items will include:
- Preparation, control and testing of programs that will be used daily on the network.
- Control over the performance and efficiency of the computers used.
- Preliminary preparation of system recovery procedures in case of errors or failures.
- Control over the fact that the subsequent installation of the new system will not have a negative impact on the network.
For all these purposes, it is necessary to prepare personnel and users.
Remote Administration Programs
If you need to control the system outside the organization, remote network administration is used. For these purposes, special software is applied, which allows you to control the system and remote access via the Internet in real time. Such programs provide almost complete control over the remote elements of the local network and each computer separately. This makes it possible to remotely manage the desktop of each computer on the network, copy or delete different files, work with programs and applications, etc.

There is a huge number of programs for remote access. All programs differ in their protocol and interface. As for the latter, the interface may have a console or visual character. Promotional and popular programs are, for example, Windows Remote Desktop, Ultravnc, Apple Remote Desktop, Remote Office Manager, etc.
Network categories
The network is a combination of various hardware, software, and communications, which are responsible for the effective distribution of information resources. All networks can be divided into three categories:
- Local.
- Global.
- Urban.
Global networks provide interaction and data exchange between users who are at large distances from each other. When working such networks, small delays in transmitting information may appear, which is caused by a relatively low data transfer rate. The length of global computer networks can reach a thousand kilometers.
Urban networks operate on a lower territory, therefore provide information on medium and high speeds. They do not slow down the data as global, but cannot transmit information over long distances. The length of such computer networks is located from several kilometers to several hundred kilometers.
Local network provides the most high speed Usually the local network is located inside one or more buildings, and its length takes no more than one kilometer. Most often, the local network is constructed for one particular organization or enterprise.
Data transmission mechanisms in different networks
The method of transmitting information in global and local networks is different. Global computer networks are primarily oriented to the connection, i.e. Before starting data transmission between two users, you must first install the connection between them. On local computer systems, other methods are used that do not require a pre-installation of communication. In this case, the information is sent to the user without receiving confirmation of its readiness.

In addition to the difference in speed, there are other differences between the specified categories of networks. If we are talking about local networks, here each computer has its own network adapter, which connects it to the rest of the computers. For the same purposes in urban networks, special dialing devices are used, while global networks use powerful routers that are connected with each other communication channels.
Network infrastructure
The computer network consists of components that can be combined into separate groups:
- Active network equipment.
- Cable system.
- Communication tools.
- Network applications.
- Network protocols.
- Network services.
Each of the specified levels has its own supends and additional components. All devices that are connected to an existing network must transmit data according to the algorithm that will be understood by other devices in the system.
Network administration tasks
Network administration foresees working with a specific system on the most different levels. If there are complex corporate networks, the following tasks cost before administration:
- Network planning. Despite the fact that in the installation of the system and the installation of all components is usually dealing with appropriate specialists, the network administrator often has to change the system, in particular, to remove or add separate components to it.
- Setting up network nodes. Administration of local networks in this case will foresee work with active most often with a network printer.
- Setting up network services. A complex network may have an extensive set of network services that include network infrastructure, directories, print files, access to databases, etc.
- Troubleshooting. Network administration foresees the skill of the search for all possible faults, ranging from problems with the router, and ending with problems in the settings of network protocols and services.
- Installations of network protocols. This includes such work as planning and subsequent configuration of network protocols, testing and defining the optimal configuration.
- Search for ways to improve the efficiency of the network. In particular, we are talking about searching for bottlenecks that require replacement of appropriate equipment.
- Monitor network nodes and network traffic.
- Ensuring information protection. This includes backing up data, user account security policy development, use of protected communication, etc.
All specified tasks must be performed in parallel and complex.
Security Administration
Security administration foresides work in several directions:
- Spread relevant informationnecessary to work security.
- Collection and analysis of data on the functioning of safety mechanisms.
Administration of local networks in this case includes work with information Base Security management. The responsibilities of the adwarestarter in this issue include the following tasks:
- Generation and redistribution of keys.
- Setting up and control access to the network.
- Encryption management with appropriate cryptoparameters.
- Configure and traffic management and routing.
The system administrator must also disseminate information among users, which is necessary for successful authentication (passwords, keys, etc.).

Protection of the system from malicious programs
Microsoft Windows has a special information security center that is responsible for protecting the system from malicious software. In addition, the operating system also has functions of protection against hacking and automatic updating of all data. Despite this, the system administrator requires the execution of additional tasks aimed at protecting the computer network:
- Access to a computer using various devices ID.
- Installing a ban on record information for removable discs.
- Encryption of removable media, etc.
Network administration is any actions aimed at implementing security policy, reliability and availability of network information resources. For these purposes, appropriate software and and on the system administrator, a number of responsibilities and tasks are headed.
The network administrator is a specialist responsible for the normal functioning and use of network resources. If more detailed, then administration Information systems include the following objectives:- Installing and setting up a network. Support for its further efficiency.
- Monitoring. System planning.
- Installing and configuring hardware devices.
- Installing software.
- Archiving (backup) information.
- Create and manage users.
- Installation and protection control.
Here is an extract of the official duties of the administrator of the network:
- Installs network software on servers and workstations.
- Configures the system on the server.
- Provides integrating software on file-servers, database management system servers and workstations.
- Supports the operating status of the server software.
- Registers users, assign identifiers and passwords.
- Trains users to work on the network, archives; responds to questions of users associated with network work; This is instructions for working with network software and brings them to username.
- Controls the use of network resources.
- Organizes access to local and global networks.
- Sets restrictions for users by:
- using a workstation or server;
- time;
- the degree of use of resources.
- Provides timely copying and backup data.
- Access to technical staff when identifying network equipment malfunctions.
- Participates in restoring the system performance in the failures and failure of network equipment.
- Receives user errors and network software and restores system performance.
- Monitoring networks, develops proposals for the development of the network infrastructure.
- Provides:
- network security (protection from unauthorized access to information, viewing or changing system files and data);
- security of firewalk.
- Prepares proposals for the modernization and acquisition of network equipment.
- Carries out control over the installation of equipment by experts of third-party organizations.
- Informs its direct supervisor on cases of abuse of the network and adopted measures.
- Leads Journal system information, other technical documentation.
- ………………………………………………………………………………………………
User groups - what is it and why?
All network users are divided into groups of groups. Each group can be responsible for performing certain tasks. It is possible to determine the rights of user groups, in which users have all the rights necessary for them to fulfill their functions, but no more. Fully all rights should be only one user - administrator (supervisor) network. It has all rights, including can create user groups and determine the rights they possess.
Users can be members at the same time multiple groups. You can, for example, create a new directory and allow access to it immediately for all network users. In this case, you will have to change access rights not for all users (there may be several dozen), but only for one group, which is significantly easier. For each laboratory or department, it makes sense to create a group of users. If you have users who need additional rights (for example, access rights to any directories or network printers), create appropriate user groups and provide them with these rights.
If there are many workstations on the network that are located in different rooms and belong to various departments or laboratories, it makes sense to create a network administrators group. The rights of several network administrators are determined by the system administrator. You should not provide network administrators of all rights of the system administrator. It is quite enough if there will be one or two administrators in each department or laboratory that have governance rights only by users in this department or laboratory. If the department or laboratory has a network printer or any other network resources, the administrator must have the right to control these devices. However, at all, at all that the administrator of one laboratory can control the network printer belonging to another laboratory. At the same time, users must have the minimum necessary access rights to the server for normal operation.
Thus, it is obvious that the creation of groups of users is relevant only in large computer networks. If the network is small, then one person will cope with such issues as adding new users, disposal of access There is no meaning to the server disks, network printers and other network resources and in the creation of groups of administrators and ordinary users.
Creating a group of users
Run on virtual Machine Server. Verify the command mMC. and add to the console tooling with which we will work - DNS, DHCP, AD users and computers. This will require a team. Console-Add or Delete Snap-Add(Fig. 55.1.
Fig. 55.1.
Now in AD, right-click and execute the command. Create a group (Fig. 55.2 and (Fig. 55.3).

Fig. 55.2.
Security group Assigns access to network resources (administer). Distribution groupcan not be administered by administration, it is engaged in sending messages. Local in the domain It may contain a user of any domain in the forest, but to administer this group can only in the domain in which the group was created. Globalmay contain users from the domain in which it was created, but they can administer any
Currently, no organization can do without computers, which are usually combined into a common local network. That is why the correct functioning of the entire computer "web" is considered vital to ensure that any information systems are correctly and fully fulfilled their functions, and the local network administration in this case becomes the main task for organizations of any structure and scale.
The service for the administration of computer networks is primarily recommended to managers of various companies and organizations, where the staff does not provide a system administrator. Now, not every company or an organization can afford to contain in the state of an experienced and professional system administrator to administer and maintain a computer network. Our specialized company understands this well, so it is ready to offer a ready-made solution - administering a locally computing network according to a compiled outsourcing agreement, which will be much cheaper and has much more indisputable advantages.
Administration features
The administration of the local network is a complex and comprehensive work consisting of different actions. It will be more obvious if you get acquainted with the list of works:
- IT audit computer network;
- Eliminate breakdowns on the local network;
- Configuring a computer network;
- Organization of protection against possible unauthorized access;
- Connecting to a network of new computers;
- Optimization and configuration of the local network routing;
- Configure Internet access and network resources.
We are ready to provide you with prompt, high-quality and professional computer help With the help of our company's employees who have practical skills and sufficient experience in administering computer networks.
We are also ready to offer you a conclusion of the Company's Network Administration Agreement, providing an operational and professional solution to emerging problems with the implementation of the computer network administration.
Preparation of contract
Before signing the contract for the administration of a computer network, it is necessary to produce its audit. According to its results, clients will be offered options for its optimization. Immediately after the fulfillment of all of the above works, if the network fails occur, a customer call specialist quickly goes to the address of the organization. The system administrator will be able to eliminate the problems of your network, either make it using remote administration.
Working with our company, you can be sure that the entire local network and IT infrastructure will always work without failures, and any faults that have arisen will be quickly eliminated. Our company is your reliable partner, which always tries to ensure uninterrupted operation of computers.