Spy KGB Spy. Allows you to establish an invisible mode of operation, so no one will guess what the most real Cailogger followed. KGB Spy. Immediately monitors the work of the computer: writes information entered from the keyboard, data from the exchange buffer, monitors visited sites.

How to detect and remove KGB Spy spy.
How to protect your personal information using the Mask S.W.B program from one of the most popular keyboard spies - KGB SPY programs.
Like computer usernot possessing knowledge in the field information security, detect the spy hidden in your system, and protect yourself from the surveillance without removing the keylogger from the computer to mislead the one who follows you? And how to remove spy KGB Spy.If you decide to do it? Consider the situation on the example of the common keyboard spy KGB Spy. and programs Mask s.w.b.which creates a protected platform for the user.
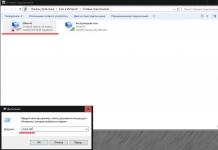
After starting the Mask S.W.B antiskon, click the System Processes button.

In the system processes window you can see all running processesexcept hidden.
To see if you have a program that is hidden on your computer, click the "Hidden Processes" button.

In the hidden processes window, scroll through the runner to the bottom. All hiding programs (rootkits) will be highlighted in red.

In the figure above, we see a spy program for name KGB Spy.. This keylogger is configured to hide your actions and follow the user.
If you want to delete KGB Spy, select "Open folder with the application" item in the context menu.

In the window that opens, run the uninstallation of the program and the spy will be deleted.

If you want to simply hide your actions from the keyboard spy and thereby mislead the one who follows you, go to the platform by clicking the button with the name of the program, as shown in the figure above.
Inside the Protection Platform, those programs that hide themselves from the user (rootkits) can be seen simply in the processes window.

Program Mask s.w.b. Creates a secure environment in which it allows you to do everything, but the behavior of the user becomes uncontrollable for spyware.

Your actions made in a protected platform will not be able to see spies - and therefore, and transfer information about them to their owners will also fail. Mask s.w.b. Protects from the removal of video from the monitor screen, from removing screenshots, does not allow to receive data from the keyboard and the clipboard. In addition, he hides websites visiting you and other information about your actions.
If you find a spy that your wife or your husband set you (well, or the boss at work), - do not rush to delete it. Think: perhaps, it is better that they think that you do not do anything to them unknown on the computer, as it will be clean in the spy. And in the meantime, you can in the platform Mask s.w.b. Do what you wish.
In the picture below, we see that the spy KGB after the actions produced in the Mask S.W.B disguise platform could not fix anything.

The program-mask is hiding the user's actions from all existing on this moment Spies. With it, you can detect and destroy computer spies operating at the level of the system drivers of the kernel and invisible for antiviruses.
Download the program Antiskon - Mask S.W.B mask and check whether the surveillance is performed using KGB SpyYou sometimes lead to the horror of the thought that your child does not depart from his computer all day, but at the same time you can't control this process!
Or recently it has liked you that your favorite person hides something from you? Nothing messages are not stored in His ICQ, all files from the computer have been transferred to the USB flash drive, it works on the Internet only when you are not there!
Sales of your company fell by 50% and best Manager Because of themselves sometimes inadequate? When you enter, he sucks something convulsion on the keyboard!
You can not understand what is happening. We do not invite you to spy for a child, a loved one or employee - we offer you a reliable assistant in obtaining the necessary information - KGB SPY keyboard spy. KGB Spy solves all secrets!
The principle of the "keyboard spy"
"How does he work?" - With surprise, you will tell you when you receive a letter with a detailed report on the user's work on a computer from KGB Spy to your electronic box. KGB Spy copes with its responsibilities even better than the famous agent 007 James Bond.
The functionality of the program allows you to establish an invisible mode of operation of KGB Spy, so no one will guess what the most real "keyboard spy" follows. KGB SPY imperceptibly monitors the operation of the computer: writes information entered from the keyboard, data from the exchange buffer, monitors visited sites.
The information collected during monitoring is stored in the database to which only you have access. You can get a letter to your email with detailed information about who, when and what did on the computer. You just need to look from time to time to your mail.

The capabilities of the spy KGB.
Comfortable and understandable interface
We tried to make the KGB SPY interface as comfortable and understandable to all, even novice computer users.
Interception of the keyboard keys
KGB Spy saves all the keys in the log that clicks the user on the keyboard.
Record screen shots (screenshots)
KGB SPY records not only the information entered from the keyboard and data from the exchange buffer, but also takes screenshots (screenshots).
Interception of ICQ, QIP, Mail.Ru Agent, etc.
KGB Spy captures all messages in the most common instant messaging programs, such as ICQ, Miranda, QIP, Yahoo! Messenger, Windows Live Messenger, Skype 3, Google Talk.
Monitoring clipboard
One of the mains functionality Programs is monitoring the content of information in the exchange buffer with which each computer user works without exception.
Monitoring visited websites
Save the company's bank account in a positive balance sheet, and Internet traffic in moderate amount - isn't it a dream of any head of the company? Make a dream with a reality with KGB Spy, which will give a full report on all user visited sites. By the way, it is also a solution to the problem for parents who are experiencing information from their information received from the Internet.
Visible / Invisible mode of operation
The program has two modes of operation: visible and invisible. Moreover, if you select an invisible mode, users will not notice the works of KGB Spy.
Monitoring startup and closing programs
Each computer, in addition to the operating system installed on it, also has a sufficient number of programs necessary in its arsenal. KGB Keylogger monitors the launch and closure of programs. This feature can be useful as to clarify the reasons for any technical problems, and to determine the timeliness or incommodation of the use of one or another software application.
Turning / off tracking / computer reset
In the XXI century, the computer has become an integral part of the life and work of any person. But in each mechanism there are tools, control the functioning of which is very difficult. KGB SPY tracks on / off / restarting a computer and allows you to quickly easily monitor the events that happen to the machine / machines.
Full multi-user support
No matter how much users in your system. KGB Spy can monitor individual, such as children or everyone.
Notifications to the e-mailbox about the set of prohibited words
If the user picks up alarm (prohibited), then KGB SPY will mark this record in a special label log or send you an email notification.
User and information system operator
In determining the presence or absence of a sanction on action with information in the information system, it is important to clearly understand the difference between the concepts of "User" (Programs or Computer) and "Operator information system" The concept of "user" is commonly used in many areas of human activity (there are the concepts of "user property", "user animals of the world", "subsoil user", "user of work", "user services", "user computer", etc.) , and the concept of "information system operator" is a special legal, defined in law and not requiring interpretation.
Let's try to figure out the user first. IN explanatory dictionary Russian Ushakov language says that the user is "a person who has in use is in operation some property", that is, on the one hand, a person using a computer can be understood under the user. However, in accordance with Art. 1280 GK, the user - "The face legally owning an instance of a program for a computer or a database instance", thus, the word "user" can also determine the owner of the program instance or database. What of these two concepts relates to our case? Since unauthorized access to information and the creation of malware should be considered only in the context of relations with information (and not relationships with intellectual property objects), the conclusion is unambiguous - in our case, it is necessary to be guided by the interpretation of the Ushakov dictionary. Consequently, in the context of the 28th chapter of the Criminal Code, the user is any person who uses the computer.
Now let's go back to the operator of the information system. According to the definition given in Article 2 of the FZ "On Information ...", "The operator of the information system is a citizen or entityoperating on the operation of the information system, including the processing of information contained in its databases. " If you are limited to this definition, you can make an incorrect output. that the "user" and "information system operator" is the same. However, in part 2 of Art. 13 of the same law: "Unless otherwise established by federal laws, the operator of the information system is the owner of the processing of technical equipment contained in the databases, which rightly uses such databases, or the person with which this owner has concluded an agreement on the operation of the information system " That is, it is not about any user, or either about the owner computer equipmentOr about the face that the owner hired to manage this technique. Thus, such as, for example, a family member of the owner home ComputerSo the firm employee working on corporate technique, being a computer user, is not an information system operator. Therefore, it is impossible to say that such a user needs to receive a sanction on access to information - he simply has no right to give such a sanction. But the owner of the home computer or the director of the company owning computer equipment, such rights have, which is unequivocally indicated in the law. Accordingly, if access to information is authorized by the information system by the operator, then the ordinary user wants or does not want this access to be carried out, this does not care anyone - the operator of the information system implements its legal right.
The main conclusion from the drawn difference is what. Read access to information without user sanction, but if there is a sanction of the information system operator (which is technical level It is implemented using the administrator password) illegal, and a program that this access is implemented, malicious, it is impossible.
If the ordinary user stores in the information system of the employer (or relative or familiar) its own information, then it, as its owner, formally has the right to allow or prohibit access to it. However, as follows from the law and practice, permission or prohibition of "technical access" to the information stored in the information system, controls its operator, and the owner of the information to intervene in the management of the information system is not entitled.
As a result, the following is obtained. If an ordinary user, like the owner of his own information, has an agreement with the operator of the information system and this contract provides that the user has the right to store its own information in someone else's information system, and the information system operator undertakes to take measures to protect against unauthorized actions, then at the end The ends of the approval on access to information in the information system still gives its operator (according to finally agreement with the owner of the information). If there is no such thing, then the user actually provides access to it to the operator of the information system, which makes it the last legal owner. From which again, it follows that it is necessary to determine the "technical access" mode to the information system will be its operator.
In our library of examples of detection and disposal spyware There are already many articles have accumulated, and we decided to classify this material.
The classification is based on a subjective assessment of technical specialists in our test laboratory. Since we are planning and in the future test popular spyware, we believe that this classification will help users of the Covert masking and visitors to our site it is better to present the place of each spyware in the mosaic of modern threats.
Every spy we give three estimates:
First - design and functionality. The higher the ball, the greater the features give the program to steal data and tracking the user.
Second - secrecy inside the system. How difficult it can be detected on the computer. The higher the ball - the better program Hides.
The third - evaluates the protection of the spy from the antispion and the complexity of its neutralization. The higher the ball, the more carefully clings to its existence on the computer and the more you need to take steps to her full removal. Some programs cannot be removed by simply erasing from the folder disk with files.
- RLM: 5/5/4
Spy VKURSE for secretly monitoring of all user actions on the computer and sending collected data to a special server. Allows hidden observation At the computer online, creates screenshots of the screen, intercepts keyboard input, clipboard and MN etc..
- RLM: 1/1 / 0
Windows Spy Keylogger is a fairly classic example of a keyboard spy - removes all keyboard input and saves in log files. It has an invisible mode, practically does not consume operating system resources, easy to install and can be installed on a computer without administrator rights.
- RLM: 3/6 / 1
SpyTector works secretly on a computer, saves passwords that were introduced in browsers and messenger Internet Explorer., Google Chrome., Opera, Firefox, Safari, Outlook, GoogleTalk, Windows Live Messenger and other applications. Keylogger can intercept whole chats in popular messengers - MSN Messenger, Yahoo Messenger, ICQ, AIM. The intercepted SpyTector Keylogger information encrypts and sends e-mail or on FTP server..
- RLM: 8/3 / 2
Jetlogger allows you to monitor user activity at a computer collects information about running programsah, visited sites and used key combinations, structures the data obtained and displays them in the form of charts and graphs. You can enable automatic creation of screen screenshots at regular intervals. Hides the fact of collecting information about the device on the device.
- RLM: 4/0/1
Yaware.timetracker is a system of working time accounting and evaluating the performance of employees at a computer.
- RLM: 5/2/3
Award Keylogger is a fairly popular spyware program that is described on many sites as a powerful tool for tracking in real time with rich functionality. But we could not see all the listed functionality, although we tested the latest full-featured version. The program turned out to be a larger than the average spy.
- RLM: 5/0/0 0
Real Spy Monitor is designed to track activity on a computer and allows you to save information about the launched files open files and windows, take the screenshots, monitor which sites are visited by users, intercept and save the keyboard input.
- RLM: 5/1/1/1
LightLogger - has enough standard set Functions - tracks visited websites, makes screenshots with a specified frequency, intercepts the keyboard input in applications, browsers and e-mail, remembers all running programs, copies the contents of the system buffer.
- RLM: 7/1 / 0
REFOG PERSONAL MONITOR will provide complete control over the system, records any keystrokes. In addition, it periodically makes screenshots, so that the observer has a full picture of what is happening on the computer. All reports are transmitted to the specified email. The work of the spy is not noticeable on the computer: he does not give out himself and consumes very few system resources.
- RLM: 5/3/3
Therat can be installed on a computer using social engineering. In addition to the traditional functions of the keyboard spy, the program can track actions in the application windows and respond to words, as well as make screenshots of the screen each time you press the ENTER key. The feature of the keylogera is the work on the principle of disembodied viruses.
- RLM: 6/2 / 1
Snitch collects user activity data and transmits them to their server from which they are already entering the control module and are displayed in its interface.
- RLM: 2/0/0 0
Hide Trace is a typical representative of screenshotters, which monitors user actions by creating a detailed report. open windows, making screenshots.
- RLM: 6/8/6
Webwatcher writes all the activity taking place on the PC: emails, Messenger messages, information about visited sites, activity in Facebook / MySpace networks and all that the user prints in real time. Removes screenshots of the screen and tracks everything search queries. All collected information It is sent to special servers on which the observer can familiarize themselves with the results of the surveillance remotely.
- RLM: 6/0 / 2
DameWare Mini Remote Control Server allows connecting and managing remote machines via the Internet or local network. It may be secretive, unnoticed for the observed, control all its actions.
— RLM: 7/2/2/2
Kickidler - the program has a good functionality, but it is easily detected and deleted. There is a function of blocking the entry into the protected Covert platform, which is easily accounted for by means of a disguise.
- RLM: 3/1 / 0
Total Spy - The interface is extremely simple, the program has a small size and does not affect the system performance. But the functionality in the program is only basic.
- RLM: 7/8/5
PC Pandora.- hides in the system and controls the entire computer and Internet traffic. Makes screenshots, gets keyboard input, actions on visited websites, email, instant messages Messengers and many more other information gathers about the user's work. The program has no folder in which it stores its data. Everything is loaded in operating system, Each new installation On the same or other computer to be made with new file names.
- RLM: 5/7/4
Micro Keylogger. - Well-hiding spyware, which is not visible in the Start menu, in the taskbar, control panels, program list, the list of MSCONFIG launch, and in other places of the computer, where it is possible to track running applications. It does not give signs of presence and do not affect system performance, secretly sends a report to email or FTP server. Its activity is conducted via DLL libraries.
- RLM: 4/0/0 0
EXPERT HOME - Multifunctional program for hidden surveillance and detailed recording of all actions manufactured on a computer with a remote tracking function that allows you to view reports and screenshots anywhere from any device, if you have access to the Internet.
- RLM: 7/0/0 0
Monitoring a remote computer in real time, makes the user's snapshots from the computer webcam, records the sounds in the room where the computer is installed, looks at file SystemRemotely downloads files, looks through and deletes system processes, and other standard functions for the spyware function.
- RLM: 5/1/1/1
SYSTEM SURVEILLANCE PRO. Provides everything you need to monitor PCs in a hidden mode. The utility registers text entry, instant messages used applications and visited sites, and also make screenshots with the specified time interval or event.
RLM: 3/0/0/0
Kidlogger Pr.This open source keylogger that can record sound from the microphone, to make screenshots. Delivery of logs / screenshots is possible by mail, or to the manufacturer's website, where they can already be viewed. It can also simply store logs with screenshots locally.
- RLM: 7/0/0 0
Remote Manipulator System - remote observation and control, allows you to connect to remote computer And manage them, as if you were sitting directly before its screen.
- RLM: 6/2 / 1
NEOSPY spy - a computer tracking program allows you to conduct hidden monitoring for the system. Tracks all actions produced by users on the monitor screen, through the Internet from the computer, smartphone and tablet.
- RLM: 6/5/3
SoftActivity Keylogger tracks and records all user actions on the computer.
It works hidden and unnoticed even for savvy users, no process in the task manager, no files cannot be seen in the system.
The configuration utility and the possibility of uninstalling are password protected.
- RLM: 4/1 / 0
Snooper - Audio Spy Designed for Recording Sounds, which catches the microphone connected to a computer, is not displayed in the recording mode, not visible in the process list in the Windows Task Manager. As long as the microphone does not lock the sounds, the spy is in sleep mode.
- RLM 5/0/1.
The Best Keylogger is a program that provides an opportunity to have always complete control over the computer.
The program allows you to read the entire history of actions on your computer in your absence.
With this program, you can view the logs of chats, as well as the mail and see the user visited on which sites.
- RLM: 5/1/1/1
Spyagent is a program for full control over user actions. Conducts the system operation monitoring, including keystrokes, running programs that are opened, and a lot more. Allows you to fix all online activity - FTP, HTTP, POP3, CHAT and other TCP / UDP communication, including visited websites. Takes pictures from the screen, sends the collected data to the specified e-mail, there is an opportunity remote control program.
- RLM: 6/2 / 0
Ardamax Keylogger - Makes Screenshots, intercepts the clipboard and pressing the keys on the keyboard. The spy has a hidden mode and it is not visible in the Task Manager. The program creates a log of all actions for subsequent analysis.
- RLM: 8/1 / 0
Spyrix Personal Monitor allows you to conduct hidden control over any activity on the computer - in social networks (VKontakte, Odnoklassniki, Facebook, etc.), chat rooms and email, visiting sites and requests in search engines (Yandex, Google). Spyrix Personal Monitor is designed for centralized monitoring of all user activities.
- RLM: 2/6/6
All In One Keylogger logs all keystrokes, including specific language symbols, conversations, and talk messages, passwords, email, exchange buffer information, microphone sounds, screenshots, online activity. The spy is not displayed in the running processes.
- RLM: 8/6/7
Mipko Personal Monitor - tracks activity on the computer, monitors which sites are visited on the Internet, saves on hDD All user actions are keystapped, visited sites, launch applications, screenshots of the screen. When working in hidden mode is not visible standard means Systems and is not displayed in the list of processes. It works absolutely unnoticed as invisible, friendly with antiviruses and in 95% of cases is not detected.
- RLM: 3/1 / 0
FREE KEYLOGGER REMOTE is able to intercept keystrokes and copied text from any applications. Also he can record names running applications, Visited websites, take screenshots at a specified period of time. The spy is valid in invisible mode and cannot be accessed. There is a function of remote monitoring and sending daily email reports.
- RLM: 7/1 / 0
SpyGo - software package For hidden monitoring and tracking user activity at a computer. Manages remotely and allows you to monitor real time. Works in hidden mode and remains invisible during the monitoring process.
- RLM: 3/1 / 0
The hidden Actual SPY agent is able to monitor all the events occurring in the system: to intercept all keystrokes, defining the register and Russian layout, take screenshots (screenshots), remember the start and closing programs, monitor the contents of the clipboard, fix connections from the Internet, Register visited sites and much more.
- RLM: 5/1/1/1
ELITE KEYLOGGER - designed to maintain secret monitoring of all types of user activity. The option of keylogger includes tracking all types of correspondence from ICQ to Email visited by users of passwords scored and used by users. The spy generates snapshots of the user's working screen. Can send a report on the actions of users to the electronic box after a certain fixed period of time.
- RLM: 6/0 / 2
Using the Power Spy utility, you can shoot at regular screenshots of the screenshot from the screen, write down the keypad, visited the Internet pages. You can also view email messages read using Microsoft Outlook. and Microsoft Outlook Express and documents opened in Word and Notepad. Program by specified parameters Sends a report on e-mail or writes to a hidden log file.
- RLM: 6/5/5
Program complex stacks @ Novec is designed to track computer Network Enterprises. It gives full information about each employee. The company's personnel monitoring can be carried out in absolutely hidden mode.
- RLM: 6/0/3
StaffCop monitors running programs, applications and websites to work PCs. Performs interception of messages in ICQ, Skype, E-mail and other messengers. Makes the monitor screen shots, writes keystrokes and much more, included in the concept of "Computer Control".
(KGB) - RLM: 7/1 / 0
KGB Spy is one of the most popular programs designed for espionage for users. personal computers. It intercepts and stores a detailed user actions on the hard disk, makes screenshots of the screen, fixes the start of software, etc.
- RLM: 1/1 / 0
Punto Switcher, designed to change the keyboard layouts in automatic mode on the computer. At the same time, it can be used as a keyboard spy if you make certain changes in settings.